1174 lines
47 KiB
Markdown
1174 lines
47 KiB
Markdown
|
|
<h1><center>大型WLAN组网部署</center></h1>
|
|||
|
|
|
|||
|
|
> 作者:行癫
|
|||
|
|
|
|||
|
|
------
|
|||
|
|
|
|||
|
|
<h3>第一节:大型WLAN组网部署</h3>
|
|||
|
|
|
|||
|
|
<h4>一:大型WLAN组网概述</h4>
|
|||
|
|
|
|||
|
|
<h5>1.大型WLAN组网的应用</h5>
|
|||
|
|
|
|||
|
|
<img src="https://xingdian-image.oss-cn-beijing.aliyuncs.com/xingdian-image/image-20220218160521941.png" alt="image-20220218160521941" style="zoom:80%;" />
|
|||
|
|
|
|||
|
|
<h5>2.大型WLAN组网特点</h5>
|
|||
|
|
|
|||
|
|
**网络规模大**
|
|||
|
|
|
|||
|
|
设备型号繁杂、分布位置广且设备数量庞大,运维成本高
|
|||
|
|
|
|||
|
|
**用户多分布广**
|
|||
|
|
|
|||
|
|
用户数量庞大,分布较广,网络体验要求高。
|
|||
|
|
|
|||
|
|
**接入安全要求高**
|
|||
|
|
|
|||
|
|
访客、员工、合作伙伴等人员会在不定期接入到内部网络,一个密码就能接入网络的场景不再适用。
|
|||
|
|
|
|||
|
|
**可靠性要求高**
|
|||
|
|
|
|||
|
|
AC控制器掌控全网的无线网络,出现故障会带来极大的经济损失。
|
|||
|
|
|
|||
|
|
<h5>3.华为大型WLAN方案功能</h5>
|
|||
|
|
|
|||
|
|
**设备统一管理 **
|
|||
|
|
|
|||
|
|
全网设备统一纳管,配置自动备份,告警实时上报,网管不再有烦恼。
|
|||
|
|
|
|||
|
|
**漫游&业务随行**
|
|||
|
|
|
|||
|
|
无缝漫游,用户在园区网络内移动时,只要身份不变,则其网络访问权限及体验将随之而动
|
|||
|
|
|
|||
|
|
**接入&终端安全保障**'
|
|||
|
|
|
|||
|
|
'准入控制技术以及终端安全防护确保安全无死角。
|
|||
|
|
|
|||
|
|
**高可靠性技术**
|
|||
|
|
|
|||
|
|
双机冷备、双机热备、N+1备份等多种高可靠性技术保障WLAN网络稳定运行。
|
|||
|
|
|
|||
|
|
<H5>4.WLAN网络解决方案</h5>
|
|||
|
|
|
|||
|
|
<img src="https://xingdian-image.oss-cn-beijing.aliyuncs.com/xingdian-image/image-20220218160913829.png" alt="image-20220218160913829" style="zoom:67%;" />
|
|||
|
|
|
|||
|
|
WLAN配合SDN控制器使用,由SDN控制器统一管理和配置,能够实现业务发放自动化、网络全生命周期管理,结合大数据和AI技术可实现园区网络的智能、极简和安全。园区网络更具备有线与无线的深度融合能力
|
|||
|
|
|
|||
|
|
<h5>5.大型WLAN网络关键技术</h5>
|
|||
|
|
|
|||
|
|
| **技术** | **作用** |
|
|||
|
|
| ------------------- | ------------------------------------------------------------ |
|
|||
|
|
| VLAN Pool | 通过VLAN Pool把接入的用户分配到不同的VLAN,可以减少广播域,减少网络中的广播报文,提升网络性能。 |
|
|||
|
|
| DHCP Option 43 & 52 | 当AC和AP间是三层组网时,AP通过发送广播请求报文的方式无法发现AC,这时需要通过DHCP服务器回应给AP的报文中携带的Option43字段(IPv4)或Option52(IPv6)来通告AC的IP地址。 |
|
|||
|
|
| 漫游技术 | WLAN漫游是指STA在不同AP覆盖范围之间移动且保持用户业务不中断的行为。 |
|
|||
|
|
| 高可靠性技术 | 为了保证WLAN业务的稳定运行,保证在主设备故障时业务能够顺利切换到备份设备的技术。 |
|
|||
|
|
| 准入控制 | 准入控制技术是通过对接入网络的客户端和用户的认证来保证网络的安全,是一种“端到端”的安全技术。 |
|
|||
|
|
|
|||
|
|
<h4>二:VLAN Pool</h4>
|
|||
|
|
|
|||
|
|
<h5>1.VLAN Pool 概念</h5>
|
|||
|
|
|
|||
|
|
**现有网络面临的挑战**
|
|||
|
|
|
|||
|
|
无线网络终端的移动性导致特定区域IP地址请求较多
|
|||
|
|
|
|||
|
|
通过情况下,一个SSID只能对应一个业务VLAN,如果通过扩大子网增加IP地址则会导致广播域扩大,大量的广播报文造成网络拥塞
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
VLAN Pool是一种把多个VLAN放在一个池中并提供分配算法的VLAN分配技术,又称为VLAN池
|
|||
|
|
|
|||
|
|
**注意:**
|
|||
|
|
|
|||
|
|
通过VLAN Pool把接入的用户分配到不同的VLAN,可以减少广播域,减少网络中的广播报文,提升网络性能
|
|||
|
|
|
|||
|
|
由于无线终端的移动性,在无线网络中经常有大量用户从某个区域接入后,随着用的移动,再漫游到其他区域,导致该区域的用户接入多,对IP地址数目要求大。比如:场馆入口、酒店的大堂等。目前一个SSID只能对应一个VLAN,一个VLAN对应一个子网,如果大量用户从某一区域接入,只能扩大VLAN的子网,保证用户能够获取到IP地址。这样带来的问题就是广播域扩大,导致大量的广播报文(如:ARP、DHCP等)带来严重的网络拥塞
|
|||
|
|
|
|||
|
|
<h5>2.VLAN Pool分配VLAN的算法</h5>
|
|||
|
|
|
|||
|
|
顺序分配算法:把用户按上线顺序依次划分到不同的VLAN中
|
|||
|
|
|
|||
|
|
HASH分配算法:根据用户MAC地址HASH值分配VLAN
|
|||
|
|
|
|||
|
|
**两种分配方式的比较:**
|
|||
|
|
|
|||
|
|
| **分配算法** | **优点** | **缺点** |
|
|||
|
|
| ------------ | ------------------------------------ | ---------------------------- |
|
|||
|
|
| 顺序分配 | 各个VLAN用户数目划分均匀 | 重新上线VLAN容易变更、IP变化 |
|
|||
|
|
| HASH分配 | 用户多次上线可分配相同的VLAN、IP不变 | 各个VLAN用户数划分不均衡 |
|
|||
|
|
|
|||
|
|
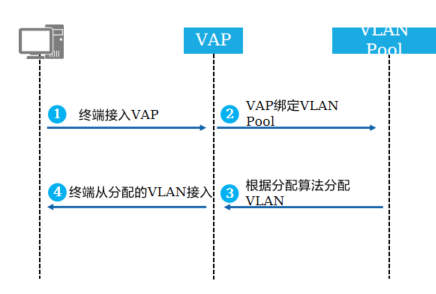
<h5>3.分配VLAN流程</h5>
|
|||
|
|
|
|||
|
|
|
|||
|
|
|
|||
|
|
用户终端从某个VAP接入,判断VAP是否有绑定VLAN Pool
|
|||
|
|
|
|||
|
|
如果该VAP对应的模板绑定了VLAN Pool,使用VLAN Pool的分配算法分配一个VLAN, VLAN Pool有顺序分配和hash分配两种分配算法
|
|||
|
|
|
|||
|
|
给终端分配一个VLAN
|
|||
|
|
|
|||
|
|
终端从VLAN Pool分配的VLAN上线
|
|||
|
|
|
|||
|
|
**注意:**
|
|||
|
|
|
|||
|
|
虚拟接入点VAP(Virtual Access Point):VAP就是在一个物理实体AP上虚拟出多个AP,每一个被虚拟出的AP就是一个VAP,每个VAP提供和物理实体AP一样的功能。用户可以在一个AP上创建不同的VAP来为不同的用户群体提供无线接入服务
|
|||
|
|
|
|||
|
|
<h5>5.VLAN Pool应用示例</h5>
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
<h5>6.配置介绍</h5>
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
<h5>7.配置案例</h5>
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
AC是STA的DHCP服务器,已开启DHCP功能
|
|||
|
|
|
|||
|
|
DHCP服务器地址包含两个网段,分别为10.1.2.0/24以及10.1.3.0/24
|
|||
|
|
|
|||
|
|
DHCP客户机能够动态获取服务器分配的IP地址,IP地址池地址范围为10.1.2.0以及10.1.3.0网段地址,且网关地址为10.1.2.254, 10.1.3.254
|
|||
|
|
|
|||
|
|
**AC的VLAN Pool配置如下:**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC] vlan pool STA
|
|||
|
|
[AC-vlan-pool-STA] vlan 20 30
|
|||
|
|
[AC-vlan-pool-STA] assignment hash
|
|||
|
|
[AC-vlan-pool-STA] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC] wlan
|
|||
|
|
[AC-wlan-view] vap-profile name huawei
|
|||
|
|
[AC-wlan-vap-prof-huawei] service-vlan vlan-pool STA
|
|||
|
|
Info: This operation may take a few seconds, please wait. Done.
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**在AC上查看所有VLAN pool下的简要配置信息:**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
<AC> display vlan pool all
|
|||
|
|
--------------------------------------------------------------------------------
|
|||
|
|
Name Assignment VLAN total
|
|||
|
|
--------------------------------------------------------------------------------
|
|||
|
|
STA hash 2
|
|||
|
|
--------------------------------------------------------------------------------
|
|||
|
|
Total: 2
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**在AC上查看STA VLAN Pool下的详细配置信息:**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
<AC> display vlan pool name STA
|
|||
|
|
--------------------------------------------------------------------------------
|
|||
|
|
Name : STA
|
|||
|
|
Total : 2
|
|||
|
|
Assignment : hash
|
|||
|
|
VLAN ID : 20 30
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
<h4>三:DHCP技术</h4>
|
|||
|
|
|
|||
|
|
<h5>1.DHCP中继</h5>
|
|||
|
|
|
|||
|
|
DHCP客户端使用IP广播来寻找同一网段上的DHCP服务器。当服务器和客户段处在不同网段,即被路由器分割开来时,路由器是不会转发这样的广播包
|
|||
|
|
|
|||
|
|
DHCP中继能够跨网段“透传”DHCP报文,使得一个DHCP服务器同时为多个网段服务成为可能
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
随着网络规模的不断扩大,网络设备不断增多,企业内不同的用户可能分布在不同的网段,一台DHCP服务器在正常情况下无法满足多个网段的地址分配需求。企业内网各个网段通常都没有与DHCP Server在同一个二层广播域内,如果还需要通过DHCP服务器分配IP地址,则需要跨网段发送DHCP协议报文
|
|||
|
|
|
|||
|
|
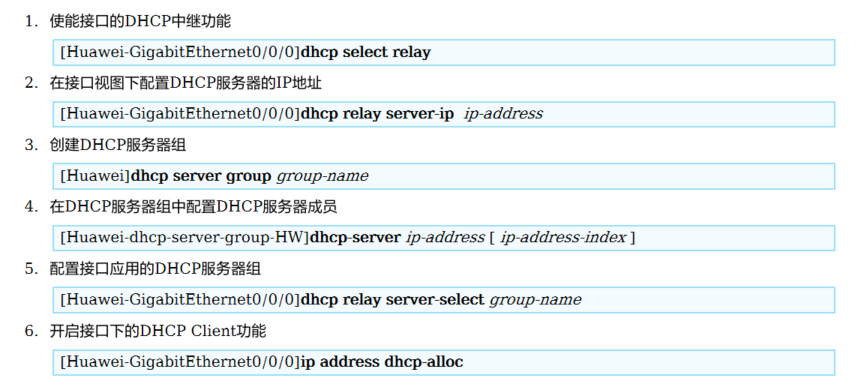
<h5>2.配置介绍</h5>
|
|||
|
|
|
|||
|
|
|
|||
|
|
|
|||
|
|
<h5>3.配置案例</h5>
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
WLAN的管理VLAN是VLAN 10,AP通过DHCP获取IP地址
|
|||
|
|
|
|||
|
|
在SW、AC和AR上配置基础互通参数
|
|||
|
|
|
|||
|
|
将AP、AC和AR分别配置为DHCP的客户端、DHCP中继以及DHCP服务器,开启DHCP功能
|
|||
|
|
|
|||
|
|
AC上开启DHCP Relay功能,并且指定DHCP Server的IP地址为172.21.1.2
|
|||
|
|
|
|||
|
|
在AR上创建地址池“AP”,地址范围为10.1.1.0/24,网关为10.1.1.2
|
|||
|
|
|
|||
|
|
**SW和AC的配置如下:**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[SW] vlan 10
|
|||
|
|
[SW-vlan10] quit
|
|||
|
|
[SW] interface GigabitEthernet 0/0/1
|
|||
|
|
[SW-GigabitEthernet0/0/1] port link-type access
|
|||
|
|
[SW-GigabitEthernet0/0/1] port default vlan 10
|
|||
|
|
[SW-GigabitEthernet0/0/1] quit
|
|||
|
|
[SW] interface GigabitEthernet 0/0/2
|
|||
|
|
[SW-GigabitEthernet0/0/2] port link-type trunk
|
|||
|
|
[SW-GigabitEthernet0/0/2] port trunk allow-pass vlan 10
|
|||
|
|
[SW-GigabitEthernet0/0/2] quit
|
|||
|
|
[SW] interface Vlanif 10
|
|||
|
|
[SW-Vlanif10] ip address 10.1.1.1 24
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC] vlan batch 10 20
|
|||
|
|
[AC] interface GigabitEthernet 0/0/1
|
|||
|
|
[AC-GigabitEthernet0/0/1] port link-type trunk
|
|||
|
|
[AC-GigabitEthernet0/0/1] port trunk allow-pass vlan 10
|
|||
|
|
[AC-GigabitEthernet0/0/1] quit
|
|||
|
|
[AC] interface GigabitEthernet 0/0/2
|
|||
|
|
[AC-GigabitEthernet0/0/1] port link-type access
|
|||
|
|
[AC-GigabitEthernet0/0/1] port default vlan 20
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**AC和AR的配置如下:**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC] interface Vlanif 10
|
|||
|
|
[AC-Vlanif10] ip address 10.1.1.2 24
|
|||
|
|
[AC-Vlanif10] quit
|
|||
|
|
[AC] interface Vlanif 20
|
|||
|
|
[AC-Vlanif20] ip address 172.21.1.1 24
|
|||
|
|
[AC-Vlanif20] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AR] interface GigabitEthernet 0/0/1
|
|||
|
|
[AR-GigabitEthernet0/0/1] ip address 172.21.1.2 24
|
|||
|
|
[AR-GigabitEthernet0/0/1] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC] dhcp server group AP
|
|||
|
|
[AC-dhcp-server-group-AP] dhcp-server 172.21.1.2
|
|||
|
|
[AC-dhcp-server-group-AP] quit
|
|||
|
|
[AC] interface Vlanif 10
|
|||
|
|
[AC-Vlanif10] dhcp select relay
|
|||
|
|
[AC-Vlanif10] dhcp relay server-select AP
|
|||
|
|
[AC-Vlanif10] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**AR的配置如下:**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AR] ip pool AP
|
|||
|
|
[AR-ip-pool-AP] network 10.1.1.0 mask 24
|
|||
|
|
[AR-ip-pool-AP] gateway-list 10.1.1.2
|
|||
|
|
[AR-ip-pool-AP] excluded-ip-address 10.1.1.1
|
|||
|
|
[AR-ip-pool-AP] quit
|
|||
|
|
[AR] interface GigabitEthernet 0/0/1
|
|||
|
|
[AR-GigabitEthernet0/0/1] dhcp select global
|
|||
|
|
[AR-GigabitEthernet0/0/1] quit
|
|||
|
|
[AR] ip route-static 10.1.1.0 255.255.255.0 172.21.1.1
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**在AR上查看DHCP地址池分配情况:**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AR] display ip pool name AP used
|
|||
|
|
……
|
|||
|
|
Network section :
|
|||
|
|
----------------------------------------------------------------------
|
|||
|
|
Index IP MAC Lease Status
|
|||
|
|
----------------------------------------------------------------------
|
|||
|
|
253 10.1.1.254 00e0-fcca-1150 2181 Used
|
|||
|
|
----------------------------------------------------------------------
|
|||
|
|
[AR]
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**在AC上查看DHCP Relay信息:**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
<AC> display dhcp relay all
|
|||
|
|
DHCP relay agent running information of interface Vlanif10 :
|
|||
|
|
Server group name : AP
|
|||
|
|
Gateway address in use : 10.1.1.2
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
<h5>4.WLAN三层组网AC发现机制</h5>
|
|||
|
|
|
|||
|
|
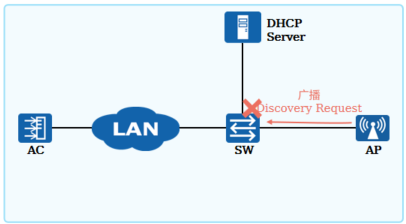
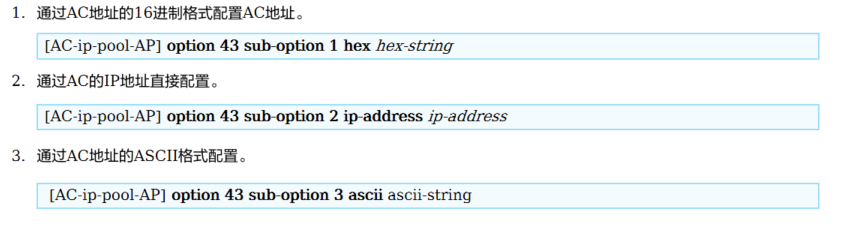
当AC和AP间是三层组网时,AP通过发送广播请求报文的方式无法发现AC,这时需要通过DHCP服务器回应给AP的报文中携带的Option43字段(IPv4)或Option52(IPv6)来通告AC的IP地址
|
|||
|
|
|
|||
|
|
|
|||
|
|
|
|||
|
|
WLAN三层组网场景,AP的广播Discovery Request报文无法发现AC,导致CAPWAP隧道无法建立
|
|||
|
|
|
|||
|
|
|
|||
|
|
|
|||
|
|
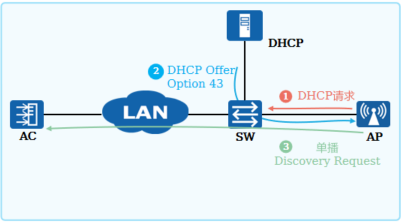
WLAN三层组网场景,配置DHCP Option 43后,在AP获取IP地址阶段,同时获取了AC的IP地址,直接通过单播与AC建立联系
|
|||
|
|
|
|||
|
|
**配置介绍**
|
|||
|
|
|
|||
|
|
|
|||
|
|
|
|||
|
|
**配置案例**
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
WLAN的管理VLAN是VLAN 10,AP通过DHCP获取IP地址
|
|||
|
|
|
|||
|
|
SW、AC以及AR的基础配置及DHCP Relay配置均已完成,AP能够正常获取到IP地址10.1.1.254,AC的IP地址为100.100.100.100
|
|||
|
|
|
|||
|
|
在AR上创建地址池“AP”,地址范围为10.1.1.0/24,网关为10.1.1.2,并添加静态路由,确保AR能够访问到10.1.1.0网段
|
|||
|
|
|
|||
|
|
**AR和AC配置如下:**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AR] ip pool AP
|
|||
|
|
[AR-ip-pool-ap] option 43 sub-option 3 ascii 100.100.100.100
|
|||
|
|
[AR-ip-pool-ap] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC] interface LoopBack 0
|
|||
|
|
[AC-LoopBack0] ip address 100.100.100.100 32
|
|||
|
|
[AC-LoopBack0] quit
|
|||
|
|
[AC] capwap source interface LoopBack 0
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**在AR上查看DHCP地址池的配置情况:**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AR] display ip pool name AP
|
|||
|
|
Pool-name : AP
|
|||
|
|
Pool-No : 0
|
|||
|
|
Lease : 1 Days 0 Hours 0 Minutes
|
|||
|
|
Option-code : 43
|
|||
|
|
Option-subcode : 3
|
|||
|
|
Option-type : ascii
|
|||
|
|
Option-value : 100.100.100.100
|
|||
|
|
……
|
|||
|
|
Position : Local Status : Unlocked
|
|||
|
|
Gateway-0 : 10.1.1.2
|
|||
|
|
Mask : 255.255.255.0
|
|||
|
|
……
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**在AC上查看AP能否正常发现AP**
|
|||
|
|
|
|||
|
|
可以看到AP已经成功发现AC,在AC上可以随时将AP添加到AC上
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC] display ap unauthorized record
|
|||
|
|
Unauthorized AP record:
|
|||
|
|
Total number: 1
|
|||
|
|
-----------------------------------------------------------------------------
|
|||
|
|
AP type: AP4030TN
|
|||
|
|
AP SN: 210235448310C92A877C
|
|||
|
|
AP MAC address: 00e0-fcca-1150
|
|||
|
|
AP IP address: 10.1.1.254
|
|||
|
|
Record time: 2020-06-18 11:51:34
|
|||
|
|
------------------------------------------------------------------------------
|
|||
|
|
[AC]
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
<h4>四:漫游技术</h4>
|
|||
|
|
|
|||
|
|
<h5>1.WLAN漫游概述</h5>
|
|||
|
|
|
|||
|
|
<img src="https://xingdian-image.oss-cn-beijing.aliyuncs.com/xingdian-image/image-20220218163644362.png" alt="image-20220218163644362" style="zoom:80%;" />
|
|||
|
|
|
|||
|
|
WLAN漫游是指STA在不同AP覆盖范围之间移动且保持用户业务不中断的行为
|
|||
|
|
|
|||
|
|
实现WLAN漫游的两个AP必须使用相同的SSID和安全模板(安全模板名称可以不同,但是安全模板下的配置必须相同),认证模板的认证方式和认证参数也要配置相同
|
|||
|
|
|
|||
|
|
**WLAN漫游策略主要解决以下问题:**
|
|||
|
|
|
|||
|
|
避免漫游过程中的认证时间过长导致丢包甚至业务中断
|
|||
|
|
|
|||
|
|
保证用户授权信息不变
|
|||
|
|
|
|||
|
|
保证用户IP地址不变
|
|||
|
|
|
|||
|
|
<h5>2.WLAN漫游的相关术语</h5>
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
AC内漫游:如果漫游过程中关联的是同一个AC,这次漫游就是AC内漫游
|
|||
|
|
|
|||
|
|
AC间漫游:如果漫游过程中关联的不是同一个AC,这次漫游就是AC间漫游
|
|||
|
|
|
|||
|
|
AC间隧道:为了支持AC间漫游,漫游组内的所有AC需要同步每个AC管理的STA和AP设备的信息,因此在AC间建立一条隧道作为数据同步和报文转发的通道。AC间隧道也是利用CAPWAP协议创建的。如图所示,AC1和AC2间建立AC间隧道进行数据同步和报文转发
|
|||
|
|
|
|||
|
|
<h5>3.WLAN漫游类型</h5>
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
二层漫游:1个无线客户端在2个AP(或多个AP)之间来回切换连接无线,前提是这些AP都绑定的是同1个SSID并且业务VLAN都在同1个VLAN内(在同一个IP地址段),漫游切换的过程中,无线客户端的接入属性(比如无线客户端所属的业务VLAN、获取的IP地址等属性)不会有任何变化,直接平滑过渡,在漫游的过程中不会有丢包和断线重连的现象
|
|||
|
|
|
|||
|
|
三层漫游:漫游前后SSID的业务VLAN不同,AP所提供的业务网络为不同的三层网络,对应不同的网关。此时,为保持漫游用户IP地址不变的特性,需要将用户流量迂回到初始接入网段的AP,实现跨VLAN漫游
|
|||
|
|
|
|||
|
|
<h5>4.WLAN漫游流量转发模型</h5>
|
|||
|
|
|
|||
|
|
| **转发模型** | **特点** |
|
|||
|
|
| ---------------- | ------------------------------------------------------------ |
|
|||
|
|
| 二层漫游直接转发 | 由于二层漫游后STA仍然在原来的子网中,所以FAP/FAC对二层漫游用户的流量转发和平台新上线的用户没有区别,直接在FAP/FAC本地的网络转发,不需要通过隧道转发回家乡代理中转。 |
|
|||
|
|
| 二层漫游隧道转发 | |
|
|||
|
|
| 三层漫游直接转发 | HAP和HAC之间的业务报文不通过CAPWAP隧道封装,无法判定HAP和HAC是否在同一个子网内,此时设备默认报文需返回到HAP进行中转。 |
|
|||
|
|
| 三层漫游隧道转发 | HAP和HAC之间的业务报文通过CAPWAP隧道封装,此时可以将HAP和HAC看作在同一个子网内,所以报文无需返回HAP,可直接通过HAC中转到上层网络。 |
|
|||
|
|
|
|||
|
|
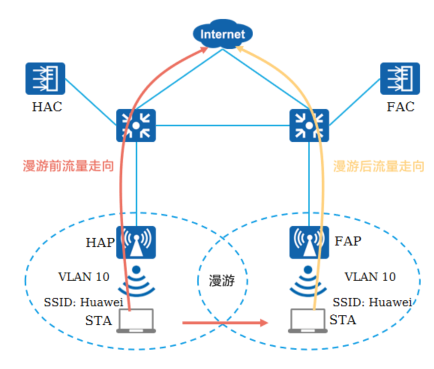
<h5>5.AC间二层漫游 - 直接转发</h5>
|
|||
|
|
|
|||
|
|
|
|||
|
|
|
|||
|
|
**漫游前:**
|
|||
|
|
|
|||
|
|
STA发送业务报文给HAP
|
|||
|
|
|
|||
|
|
HAP接收到业务报文后经由网关(交换机)发送给上层网络
|
|||
|
|
|
|||
|
|
**漫游后:**
|
|||
|
|
|
|||
|
|
STA发送业务报文给FAP
|
|||
|
|
|
|||
|
|
FAP接收到业务报文后经由网关(交换机)发送给上层网络
|
|||
|
|
|
|||
|
|
<h5>6.AC间三层漫游 - 隧道转发</h5>
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
**漫游前:**
|
|||
|
|
|
|||
|
|
STA发送业务报文给HAP
|
|||
|
|
|
|||
|
|
HAP接收到业务报文后通过CAPWAP隧道发送给HAC
|
|||
|
|
|
|||
|
|
HAC直接将业务报文经过交换机发送给上层网络
|
|||
|
|
|
|||
|
|
**漫游后:**
|
|||
|
|
|
|||
|
|
STA发送业务报文给FAP
|
|||
|
|
|
|||
|
|
FAP接收到业务报文后通过CAPWAP隧道发送给FAC
|
|||
|
|
|
|||
|
|
FAC通过HAC和FAC之间的AC间隧道将业务报文转发给HAC
|
|||
|
|
|
|||
|
|
HAC直接将业务报文经由交换机发送给上层网络
|
|||
|
|
|
|||
|
|
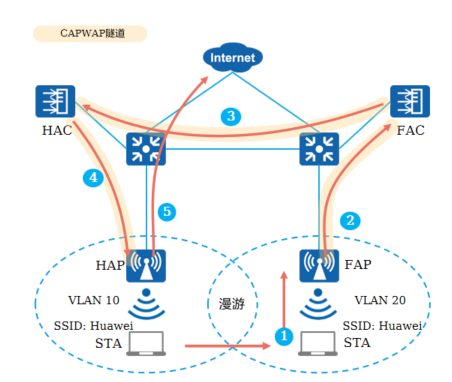
<h5>7.AC间三层漫游 - 直接转发(HAP为家乡代理)</h5>
|
|||
|
|
|
|||
|
|
|
|||
|
|
|
|||
|
|
**漫游前:**
|
|||
|
|
|
|||
|
|
STA发送业务报文给HAP
|
|||
|
|
|
|||
|
|
HAP接收到业务报文后直接将业务报文经过交换机发送给上层网络
|
|||
|
|
|
|||
|
|
**漫游后:**
|
|||
|
|
|
|||
|
|
STA发送业务报文给FAP
|
|||
|
|
|
|||
|
|
FAP接收到STA发送的业务报文并通过CAPWAP隧道发送给FAC
|
|||
|
|
|
|||
|
|
FAC通过HAC和FAC之间的AC间隧道将业务报文转发给HAC
|
|||
|
|
|
|||
|
|
HAC通过CAPWAP隧道将业务报文发送给HAP
|
|||
|
|
|
|||
|
|
HAP直接将业务报文发送给上层网络
|
|||
|
|
|
|||
|
|
<h5>8.AC间三层漫游 - 直接转发(HAC为家乡代理)</h5>
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
**漫游前:**
|
|||
|
|
|
|||
|
|
STA发送业务报文给HAP
|
|||
|
|
|
|||
|
|
HAP接收到业务报文后直接将业务报文经过交换机发送给上层网络
|
|||
|
|
|
|||
|
|
**漫游后:**
|
|||
|
|
|
|||
|
|
STA发送业务报文给FAP
|
|||
|
|
|
|||
|
|
FAP接收到STA发送的业务报文并通过CAPWAP隧道发送给FAC
|
|||
|
|
|
|||
|
|
FAC通过HAC和FAC之间的AC间隧道将业务报文转发给HAC
|
|||
|
|
|
|||
|
|
HAC直接将业务报文发送给上层网络
|
|||
|
|
|
|||
|
|
<h5>9.AC间漫游配置介绍</h5>
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
**配置漫游组**
|
|||
|
|
|
|||
|
|
如果指定了漫游组服务器,则需要在漫游组服务器上配置漫游组
|
|||
|
|
|
|||
|
|
如果没有指定漫游组服务器,则各成员AC均需配置漫游组
|
|||
|
|
|
|||
|
|
<h5>10.配置案例</h5>
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
HAP与HAC,FAP与FAC之间的组网方式为三层组网
|
|||
|
|
|
|||
|
|
配置HAC和FAC形成漫游组,保证STA的业务流量正常
|
|||
|
|
|
|||
|
|
**配置AC1和AC2的WLAN漫游功能:**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC1-wlan-view] mobility-group name mobility
|
|||
|
|
[AC1-mc-mg-mobility] member ip-address 10.1.201.100
|
|||
|
|
[AC1-mc-mg-mobility] member ip-address 10.1.201.200
|
|||
|
|
[AC1-mc-mg-mobility] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC2-wlan-view] mobility-group name mobility
|
|||
|
|
[AC2-mc-mg-mobility] member ip-address 10.1.201.100
|
|||
|
|
[AC2-mc-mg-mobility] member ip-address 10.1.201.200
|
|||
|
|
[AC2-mc-mg-mobility] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**STA漫游后在AC2上查看STA的漫游轨迹:**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
<AC> display station roam-track sta-mac 28b2-bd35-4af3
|
|||
|
|
Access SSID:huawei-guest1
|
|||
|
|
Rx/Tx: Rx-Rate/Tx-Rate Mbps
|
|||
|
|
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------
|
|||
|
|
L2/L3 AC IP AP name Radio ID BSSID TIME In Rx/Tx RSSI Out Rx/Tx RSSI
|
|||
|
|
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------
|
|||
|
|
-- 10.1.201.100 ap1 1 cccc-8110-2250 2020/06/18 14:09:06 130/130 -44 130/130 -44
|
|||
|
|
L3 10.1.201.200 ap2 1 cccc-8110-22b0 2020/06/18 14:12:24 130/6 -42 -/-
|
|||
|
|
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------
|
|||
|
|
Number of roam track: 1
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
<h4>五:高可靠性技术</h4>
|
|||
|
|
|
|||
|
|
<h5>1.AC高可靠性概述</h5>
|
|||
|
|
|
|||
|
|
**在WLAN组网中,为保证组网可靠性,常见的备份技术有:**
|
|||
|
|
|
|||
|
|
VRRP双机热备份(主备)
|
|||
|
|
|
|||
|
|
双链路冷备份
|
|||
|
|
|
|||
|
|
双链路热备份(主备&负载分担)
|
|||
|
|
|
|||
|
|
N+1备份
|
|||
|
|
|
|||
|
|
为了保证WLAN业务的稳定运行,热备份(Hot-Standby Backup)机制可以保证在主设备故障时业务能够不中断的顺利切换到备份设备
|
|||
|
|
|
|||
|
|
**注意:**
|
|||
|
|
|
|||
|
|
热备份是指,当两台设备在确定主用(Master)设备和备用(Backup)设备后,由主用设备进行业务的转发,而备用设备处于监控状态,同时主用设备实时向备用设备发送状态信息和需要备份的信息,当主用设备出现故障后,备用设备及时接替主用设备的业务运行
|
|||
|
|
|
|||
|
|
**VRRP双机热备份**
|
|||
|
|
|
|||
|
|
主备AC两个独立的IP地址,通过VRRP对外虚拟为同一个IP地址,单个AP和虚拟IP建立一条CAPWAP链路
|
|||
|
|
|
|||
|
|
主AC备份AP信息、STA信息和CAPWAP链路信息,并通过HSB主备服务将信息同步给备AC。主AC故障后,备AC直接接替工作
|
|||
|
|
|
|||
|
|
**双链路热备份**
|
|||
|
|
|
|||
|
|
单个AP分别和主备AC建立CAPWAP链路,一条主链路,一条备链路
|
|||
|
|
|
|||
|
|
主AC仅备份STA信息,并通过HSB主备服务将信息同步给备AC。主AC故障后,AP切换到备链路上,备AC接替工作
|
|||
|
|
|
|||
|
|
**双链路冷备份**
|
|||
|
|
|
|||
|
|
单个AP分别和主备AC建立CAPWAP链路,一条主链路,一条备链路
|
|||
|
|
|
|||
|
|
AC不备份同步信息。主AC故障后,AP切换到备链路上,备AC接替工作
|
|||
|
|
|
|||
|
|
**N+1备份**
|
|||
|
|
|
|||
|
|
单个AP只和一个AC建立CAPWAP链路
|
|||
|
|
|
|||
|
|
AC不备份同步信息。主AC故障后,AP重新与备AC建链CAPWAP链路,备AC接替工作
|
|||
|
|
|
|||
|
|
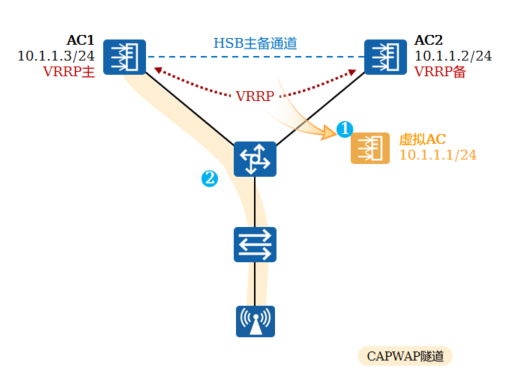
<h5>2.VRRP双机热备</h5>
|
|||
|
|
|
|||
|
|
|
|||
|
|
|
|||
|
|
两台AC组成一个VRRP组,主、备AC对AP始终显示为同一个虚拟IP地址,主AC通过Hot Standby(HSB)主备通道同步业务信息到备AC上
|
|||
|
|
|
|||
|
|
两台AC通过VRRP协议产生一台“虚拟AC”,缺省情况下,主AC担任虚拟AC的具体工作,当主AC故障时,备AC接替其工作。所有AP与“虚拟AC”建立CAPWAP隧道
|
|||
|
|
|
|||
|
|
AP只看到一个AC的存在,AC间的切换由VRRP决定
|
|||
|
|
|
|||
|
|
这种方式一般将主备AC部署在同一地理位置,和其他备份方式比较,其业务切换速度非常快
|
|||
|
|
|
|||
|
|
**HSB相关概念**
|
|||
|
|
|
|||
|
|
HSB(Hot Standby,热备份)是华为主备公共机制
|
|||
|
|
|
|||
|
|
主备服务(HSB service):建立和维护主备通道,为各个主备业务模块提供通道通断事件和报文发送/接收接口
|
|||
|
|
|
|||
|
|
主备备份组(HSB group):HSB备份组内部绑定HSB service,为各个主备业务模块提供数据备份通道。HSB备份组与一个VRRP实例绑定,借用VRRP机制协商出主备实例。同时,HSB备份组还负责通知各个业务模块处理批量备份、实时备份、主备切换等事件
|
|||
|
|
|
|||
|
|
**HSB主备服务**
|
|||
|
|
|
|||
|
|
HSB主备服务负责在两个互为备份的设备间建立主备备份通道,维护主备通道的链路状态,为其他业务提供报文的收发服务,并在备份链路发生故障时通知主备业务备份组进行相应的处理
|
|||
|
|
|
|||
|
|
HSB主备服务主要包括两个方面:
|
|||
|
|
|
|||
|
|
建立主备备份通道
|
|||
|
|
|
|||
|
|
维护主备通道的链路状态
|
|||
|
|
|
|||
|
|
**数据同步**
|
|||
|
|
|
|||
|
|
基于VRRP双机热备备份信息包括用户表项、CAPWAP链路信息以及AP表项等信息,备份的方式有实时备份,批量备份,定时备份
|
|||
|
|
|
|||
|
|
批量备份:主用设备会将已有的会话表项一次性同步到新加入的备份设备上,使主备AC信息对齐,这个过程称为批量备份。批量备份会在AC主备确立时进行触发
|
|||
|
|
|
|||
|
|
实时备份:主用设备在产生新表项或表项变化后会及时备份到备份设备上
|
|||
|
|
|
|||
|
|
定时同步:备用设备会每隔30分钟检查其已有的会话表项与主用设备是否一致,若不一致则将主用设备上的会话表项同步到备用设备
|
|||
|
|
|
|||
|
|
**VRRP双机热备配置流程**
|
|||
|
|
|
|||
|
|
<img src="https://xingdian-image.oss-cn-beijing.aliyuncs.com/xingdian-image/image-20220218170114006.png" alt="image-20220218170114006" style="zoom:50%;" />
|
|||
|
|
|
|||
|
|
创建VRRP备份组并配置虚拟IP地址
|
|||
|
|
|
|||
|
|
创建HSB主备服务,建立HSB主备备份通道的IP地址和端口号
|
|||
|
|
|
|||
|
|
创建HSB备份组,配置HSB备份组绑定HSB主备服务、VRRP备份组、WLAN业务以及DHCP
|
|||
|
|
|
|||
|
|
使能HSB备份组,HSB备份组使能后,对HSB备份组的相关配置才会生效
|
|||
|
|
|
|||
|
|
检查VRRP热备份配置结果
|
|||
|
|
|
|||
|
|
**配置介绍**
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
**配置案例**
|
|||
|
|
|
|||
|
|
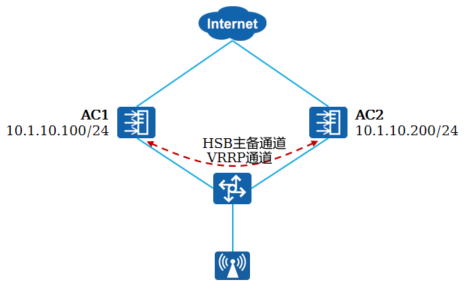
|
|||
|
|
|
|||
|
|
AC1和AC2通过VLANIF10建立VRRP主备关系,VRRP的虚拟IP为10.1.10.1,AC1为主设备,且优先级为120
|
|||
|
|
|
|||
|
|
使用HSB技术实现双机热备
|
|||
|
|
|
|||
|
|
AC的VRRP配置如下:
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC1]interface Vlanif10
|
|||
|
|
[AC1-Vlanif10]ip address 10.1.10.100 255.255.255.0
|
|||
|
|
[AC1-Vlanif10]vrrp vrid 1 virtual-ip 10.1.10.1
|
|||
|
|
[AC1-Vlanif10]vrrp vrid 1 priority 120
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC2]interface Vlanif10
|
|||
|
|
[AC2-Vlanif10]ip address 10.1.10.200 255.255.255.0
|
|||
|
|
[AC2-Vlanif10]vrrp vrid 1 virtual-ip 10.1.10.1
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
AC的HSB配置如下:
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC1]hsb-service 0
|
|||
|
|
[AC1-hsb-service-0]service-ip-port local-ip 10.1.10.100 peer-ip 10.1.10.200 local-data-port 10241 peer-data-port 10241
|
|||
|
|
[AC1-hsb-service-0]quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC1]hsb-group 0
|
|||
|
|
[AC1-hsb-group-0]bind-service 0
|
|||
|
|
[AC1-hsb-group-0]track vrrp vrid 1 interface Vlanif10
|
|||
|
|
[AC1-hsb-group-0]quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC1]hsb-service-type access-user hsb-group 0
|
|||
|
|
[AC1]hsb-service-type dhcp hsb-group 0
|
|||
|
|
[AC1]hsb-service-type ap hsb-group 0
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC1]hsb-group 0
|
|||
|
|
[AC1-hsb-group-0]hsb enable
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**在AC上查看主备服务的建立情况**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC1] display hsb-service 0
|
|||
|
|
Hot Standby Service Information:
|
|||
|
|
----------------------------------------------------------
|
|||
|
|
Local IP Address : 10.1.10.100
|
|||
|
|
Peer IP Address : 10.1.10.200
|
|||
|
|
Source Port : 10241
|
|||
|
|
Destination Port : 10241
|
|||
|
|
Keep Alive Times : 2
|
|||
|
|
Keep Alive Interval : 1
|
|||
|
|
Service State : Connected
|
|||
|
|
Service Batch Modules :
|
|||
|
|
Shared-key : -
|
|||
|
|
----------------------------------------------------------
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**在AC上查看HSB备份组的运行情况**
|
|||
|
|
|
|||
|
|
```shell
|
|||
|
|
[AC1] display hsb-group 0
|
|||
|
|
Hot Standby Group Information:
|
|||
|
|
----------------------------------------------------------
|
|||
|
|
HSB-group ID : 0
|
|||
|
|
Vrrp Group ID : 1
|
|||
|
|
Vrrp Interface : Vlanif10
|
|||
|
|
Service Index : 0
|
|||
|
|
Group Vrrp Status : Master
|
|||
|
|
Group Status : Active
|
|||
|
|
Group Backup Process : Realtime
|
|||
|
|
Peer Group Device Name : AirEngine 9700-M
|
|||
|
|
Peer Group Software Version : V200R019C00
|
|||
|
|
Group Backup Modules : Access-user
|
|||
|
|
DHCP
|
|||
|
|
AP
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
<h5>3.双链路双机热备</h5>
|
|||
|
|
|
|||
|
|
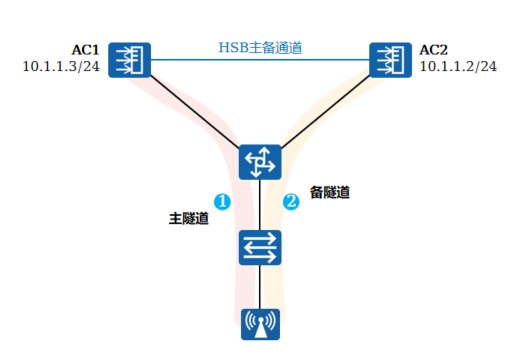
|
|||
|
|
|
|||
|
|
双链路双机热备场景下,业务直接绑定HSB备份服务,这样HSB对业务仅提供备份数据收发的功能,用户的主备状态由双链路机制进行维护
|
|||
|
|
|
|||
|
|
AP同时与主备AC之间分别建立CAPWAP隧道,AC间的业务信息通过HSB主备通道同步
|
|||
|
|
|
|||
|
|
当AP和主AC间链路断开,AP会通知备AC切换成主AC
|
|||
|
|
|
|||
|
|
**主备协商&建立主链路**
|
|||
|
|
|
|||
|
|
<img src="https://xingdian-image.oss-cn-beijing.aliyuncs.com/xingdian-image/image-20220218170625999.png" alt="image-20220218170625999" style="zoom:80%;" />
|
|||
|
|
|
|||
|
|
**AP与AC建立主链路,在Discovery阶段要优选出主AC**
|
|||
|
|
|
|||
|
|
使能双链路备份功能后,AP开始发送Discovery Request报文
|
|||
|
|
|
|||
|
|
AC收到Request报文后回应Discovery Response报文
|
|||
|
|
|
|||
|
|
AP收集到主备AC回应的Discovery Response报文后,根据AC的优先级、设备的负载情况以及AC的IP地址来选择主AC
|
|||
|
|
|
|||
|
|
AP开始与优选出的主AC建立CAPWAP主链路
|
|||
|
|
|
|||
|
|
**建立备链路**
|
|||
|
|
|
|||
|
|
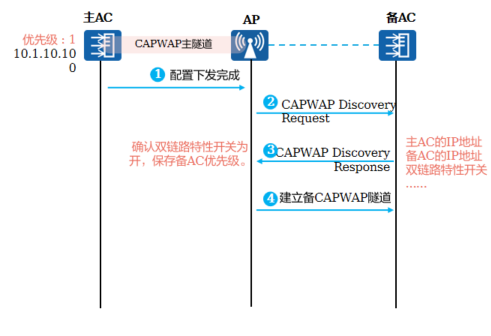
|
|||
|
|
|
|||
|
|
AP与AC建立备链路,为了避免业务配置重复下发导致错误,在AP和 主AC建立主隧道并且配置下发完成后,才启动备CAPWAP链路的建立
|
|||
|
|
|
|||
|
|
主AC下发配置到AP上
|
|||
|
|
|
|||
|
|
AP开始建立备用隧道,向备AC发送单播CAPWAP Discovery Request报文
|
|||
|
|
|
|||
|
|
备AC收到Request报文后,回应Response报文,在该报文中携带优选AC的IP地址、备选AC的IP地址、双链路特性开关、负载情况及其优先级
|
|||
|
|
|
|||
|
|
AP收到备AC回应的Response报文后,获取到双链路特性开关为打开,并保存其优先级
|
|||
|
|
|
|||
|
|
**配置介绍**
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
**配置案例 **
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
AC1和AC2配置双链路双机热备,AC1为主设备,优先级为1,AC2为备设备,优先级为2
|
|||
|
|
|
|||
|
|
使用HSB技术实现双机热备
|
|||
|
|
|
|||
|
|
AC1的配置如下:
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC1] wlan
|
|||
|
|
[AC1-wlan-view] ac protect enable
|
|||
|
|
[AC1-wlan-view] ac protect protect-ac 10.1.10.200 priority 1
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC1] hsb-service 0
|
|||
|
|
[AC1-hsb-service-0] service-ip-port local-ip 10.1.10.100 peer-ip 10.1.10.200 local-data-port 10241 peer-data-port 10241
|
|||
|
|
[AC1-hsb-service-0] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC1] hsb-service-type access-user hsb-group 0
|
|||
|
|
[AC1] hsb-service-type dhcp hsb-group 0
|
|||
|
|
[AC1] hsb-service-type ap hsb-group 0
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
AC2的配置如下:
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC2] wlan
|
|||
|
|
[AC2-wlan-view] ac protect enable
|
|||
|
|
[AC2-wlan-view] ac protect protect-ac 10.1.10.100 priority 2
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC2] hsb-service 0
|
|||
|
|
[AC2-hsb-service-0] service-ip-port local-ip 10.1.10.200 peer-ip 10.1.10.100 local-data-port 10241 peer-data-port 10241
|
|||
|
|
[AC2-hsb-service-0] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC2] hsb-service-type access-user hsb-group 0
|
|||
|
|
[AC2] hsb-service-type dhcp hsb-group 0
|
|||
|
|
[AC2] hsb-service-type ap hsb-group 0
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**在AC上查看双链路备份的配置信息**
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC1] display ac protect
|
|||
|
|
------------------------------------------------------------
|
|||
|
|
Protect state : enable
|
|||
|
|
Protect AC IPv4 : 10.1.10.200
|
|||
|
|
Protect AC IPv6 : -
|
|||
|
|
Priority : 0
|
|||
|
|
Protect restore : enable
|
|||
|
|
...
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**在AC上查看主备服务的建立情况**
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC1] display hsb-service 0
|
|||
|
|
Hot Standby Service Information:
|
|||
|
|
----------------------------------------------------------
|
|||
|
|
Local IP Address : 10.1.10.100
|
|||
|
|
Peer IP Address : 10.1.10.200
|
|||
|
|
Source Port : 10241
|
|||
|
|
Destination Port : 10241
|
|||
|
|
Keep Alive Times : 5
|
|||
|
|
Keep Alive Interval : 3
|
|||
|
|
Service State : Connected
|
|||
|
|
Service Batch Modules : AP
|
|||
|
|
Access-user
|
|||
|
|
DHCP
|
|||
|
|
……
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
<h5>4.AC可靠性:N+1</h5>
|
|||
|
|
|
|||
|
|
<img src="https://xingdian-image.oss-cn-beijing.aliyuncs.com/xingdian-image/image-20220218173250554.png" alt="image-20220218173250554" style="zoom:80%;" />
|
|||
|
|
|
|||
|
|
N+1备份是指在AC+FIT AP的网络架构中,使用一台AC作为备AC,为多台主AC提供备份服务的一种解决方案
|
|||
|
|
|
|||
|
|
网络正常情况下,AP只与各自所属的主AC建立CAPWAP链路
|
|||
|
|
|
|||
|
|
当主AC故障或主AC与AP间CAPWAP链路故障时,备AC替代主AC来管理AP,备AC与AP间建立CAPWAP链路,为AP提供业务服务
|
|||
|
|
|
|||
|
|
支持主备倒换,支持主备回切
|
|||
|
|
|
|||
|
|
**N+1 备份—主备选择**
|
|||
|
|
|
|||
|
|
<img src="https://xingdian-image.oss-cn-beijing.aliyuncs.com/xingdian-image/image-20220218173353652.png" alt="image-20220218173353652" style="zoom:80%;" />
|
|||
|
|
|
|||
|
|
在Discovery阶段,AP发现AC后,要选择出最高优先级的AC作为主AC接入
|
|||
|
|
|
|||
|
|
AC上存在两种优先级:
|
|||
|
|
|
|||
|
|
全局优先级:针对所有AP配置的AC优先级,默认为0,最大值为7,优先级取值越小,优先级越高
|
|||
|
|
|
|||
|
|
个性优先级:针对指定的单个AP或指定AP组中的AP配置的AC优先级,没有默认值
|
|||
|
|
|
|||
|
|
AC全局优先级<AP在AC上优先级
|
|||
|
|
|
|||
|
|
注意:
|
|||
|
|
|
|||
|
|
当AC收到AP发送的Discovery Request报文时,如果AC没有为该AP配置个性优先级,则在回应的Discovery Response报文中携带全局优先级
|
|||
|
|
|
|||
|
|
如果AC已为该AP配置了个性优先级,则在回应的Discovery Response报文中携带个性优先级
|
|||
|
|
|
|||
|
|
正确配置主AC和备AC的不同优先级,可以控制AP能够在指定的主AC或备AC上线
|
|||
|
|
|
|||
|
|
优选顺序如下:
|
|||
|
|
|
|||
|
|
AP查看优选AC,如果只有一个优选AC,则此AC作为主AC。如果存在多个优选AC,则选择负载最轻的AC作为主AC,如果负载相同选择IP地址最小的作为主AC
|
|||
|
|
|
|||
|
|
负载的比较方式:比较AC设备的负载情况,即AP个数和STA个数,负载轻的为主AC。优先选择当前可接入AP数大的AC为主AC,如果当前可接入AP数相同,则选择当前可接入STA数大的AC为主AC
|
|||
|
|
|
|||
|
|
如果没有优选AC,查看备选AC,如果只有一个备选AC,则此AC作为主AC,如果存在多个备选AC,则选择负载最轻的AC作为主AC,如果负载相同选择IP地址最小的作为主AC
|
|||
|
|
|
|||
|
|
如果没有备选AC,比较AC的优先级,优先级最高的作为主AC。优先级取值越小,优先级越高。优先级的具体判断方式参考主备优先级
|
|||
|
|
|
|||
|
|
优先级相同情况下,则选择负载最轻的AC作为主AC
|
|||
|
|
|
|||
|
|
负载相同情况下,继续比较IP地址,IP地址小的为主AC
|
|||
|
|
|
|||
|
|
**配置介绍**
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
**配置案例**
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
已经完成各个AC和其它网络设备实现网络互通的配置
|
|||
|
|
|
|||
|
|
AC1作为AP1的主AC,AC2作为AP2的主AC,在主AC上配置主备AC信息
|
|||
|
|
|
|||
|
|
AC3作为AP1和AP2的备AC,在备AC上配置两个AP组,保持WLAN基本业务,业务配置和主AC保持一致
|
|||
|
|
|
|||
|
|
先后在主备AC上配置N+1备份功能。配置完成后需要重启所有AP
|
|||
|
|
|
|||
|
|
AC1的配置如下:
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC1-wlan-view] ap-system-profile name ap-system1
|
|||
|
|
[AC1-wlan-ap-system-prof-ap-system1] primary-access ip-address 10.23.201.1
|
|||
|
|
[AC1-wlan-ap-system-prof-ap-system1] backup-access ip-address 10.23.203.1
|
|||
|
|
[AC1-wlan-ap-system-prof-ap-system1] quit
|
|||
|
|
[AC1-wlan-view] ap-group name ap-group1
|
|||
|
|
[AC1-wlan-ap-group-ap-group1] ap-system-profile ap-system1
|
|||
|
|
[AC1-wlan-ap-group-ap-group1] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC2-wlan-view] ap-system-profile name ap-system2
|
|||
|
|
[AC2-wlan-ap-system-prof-ap-system2] primary-access ip-address 10.23.202.1
|
|||
|
|
[AC2-wlan-ap-system-prof-ap-system2] backup-access ip-address 10.23.203.1
|
|||
|
|
[AC2-wlan-ap-system-prof-ap-system2] quit
|
|||
|
|
[AC2-wlan-view] ap-group name ap-group2
|
|||
|
|
[AC2-wlan-ap-group-ap-group2] ap-system-profile ap-system2
|
|||
|
|
[AC2-wlan-ap-group-ap-group2] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
AC3的配置如下:
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC3-wlan-view] ap-system-profile name ap-system1
|
|||
|
|
[AC3-wlan-ap-system-prof-ap-system1] primary-access ip-address 10.23.201.1
|
|||
|
|
[AC3-wlan-ap-system-prof-ap-system1] backup-access ip-address 10.23.203.1
|
|||
|
|
[AC3-wlan-ap-system-prof-ap-system1] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC3-wlan-view] ap-system-profile name ap-system2
|
|||
|
|
[AC3-wlan-ap-system-prof-ap-system2] primary-access ip-address 10.23.202.1
|
|||
|
|
[AC3-wlan-ap-system-prof-ap-system2] backup-access ip-address 10.23.203.1
|
|||
|
|
[AC3-wlan-ap-system-prof-ap-system2] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC3-wlan-view] ap-group name ap-group1
|
|||
|
|
[AC3-wlan-ap-group-ap-group1] ap-system-profile ap-system1
|
|||
|
|
[AC3-wlan-ap-group-ap-group1] quit
|
|||
|
|
[AC3-wlan-view] ap-group name ap-group2
|
|||
|
|
[AC3-wlan-ap-group-ap-group2] ap-system-profile ap-system2
|
|||
|
|
[AC3-wlan-ap-group-ap-group2] quit
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
AC的配置如下:
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC1-wlan-view] undo ac protect enable
|
|||
|
|
Info: Backup function has already disabled.
|
|||
|
|
[AC1-wlan-view] ap-reset all
|
|||
|
|
Warning: Reset AP(s), continue?[Y/N]: y
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC2-wlan-view] undo ac protect enable
|
|||
|
|
Info: Backup function has already disabled.
|
|||
|
|
[AC2-wlan-view] ap-reset all
|
|||
|
|
Warning: Reset AP(s), continue?[Y/N]: y
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC3-wlan-view] undo ac protect restore disable
|
|||
|
|
Info: Protect restore has already enabled.
|
|||
|
|
[AC3-wlan-view] undo ac protect enable
|
|||
|
|
Info: Backup function has already disabled.
|
|||
|
|
[AC3-wlan-view] ap-reset all
|
|||
|
|
Warning: Reset AP(s), continue?[Y/N]: y
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**在主AC1上查看AC上N+1备份信息**
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC1] display ac protect
|
|||
|
|
------------------------------------------------------------
|
|||
|
|
Protect state : disable
|
|||
|
|
Protect AC IPv4 : -
|
|||
|
|
Protect AC IPv6 : -
|
|||
|
|
Priority : 0
|
|||
|
|
Protect restore : enable
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC1] display ap-system-profile name ap-system
|
|||
|
|
---------------------------------------------------------------------------
|
|||
|
|
AC priority : -
|
|||
|
|
Protect AC IP address : -
|
|||
|
|
Primary AC : 10.23.201.1
|
|||
|
|
Backup AC : 10.23.203.1
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**在主AC2上查看AC上N+1备份信息**
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC2] display ac protect
|
|||
|
|
------------------------------------------------------------
|
|||
|
|
Protect state : disable
|
|||
|
|
Protect AC IPv4 : -
|
|||
|
|
Protect AC IPv6 : -
|
|||
|
|
Priority : 0
|
|||
|
|
Protect restore : enable
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC2] display ap-system-profile name ap-system
|
|||
|
|
---------------------------------------------------------------------------
|
|||
|
|
AC priority : -
|
|||
|
|
Protect AC IP address : -
|
|||
|
|
Primary AC : 10.23.202.1
|
|||
|
|
Backup AC : 10.23.203.1
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
**在备AC3上,查看AC上N+1备份信息**
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC3] display ac protect
|
|||
|
|
------------------------------------------------------------
|
|||
|
|
Protect state : disable
|
|||
|
|
Protect AC IPv4 : -
|
|||
|
|
Protect AC IPv6 : -
|
|||
|
|
Priority : 0
|
|||
|
|
Protect restore : enable
|
|||
|
|
...
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC3-wlan-view] display ap-system-profile name ap-system1
|
|||
|
|
---------------------------------------------------------------------------
|
|||
|
|
AC priority : -
|
|||
|
|
Protect AC IP address : -
|
|||
|
|
Primary AC : 10.23.201.1
|
|||
|
|
Backup AC : 10.23.203.1
|
|||
|
|
...
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
```
|
|||
|
|
[AC3-wlan-view] display ap-system-profile name ap-system2
|
|||
|
|
---------------------------------------------------------------------------
|
|||
|
|
AC priority : -
|
|||
|
|
Protect AC IP address : -
|
|||
|
|
Primary AC : 10.23.202.1
|
|||
|
|
Backup AC : 10.23.203.1
|
|||
|
|
...
|
|||
|
|
```
|
|||
|
|
|
|||
|
|
<h4>六:准入控制技术</h4>
|
|||
|
|
|
|||
|
|
<h5>1.NAC概述</h5>
|
|||
|
|
|
|||
|
|
NAC(Network Admission Control)称为网络接入控制,通过对接入网络的客户端和用户的认证保证网络的安全,是一种“端到端”的安全技术
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
**NAC:**
|
|||
|
|
|
|||
|
|
用于用户和接入设备之间的交互
|
|||
|
|
|
|||
|
|
NAC负责控制用户的接入方式(802.1X,MAC或Portal认证),接入过程中的各类参数和定时器
|
|||
|
|
|
|||
|
|
确保合法用户和接入设备建立安全稳定的连接
|
|||
|
|
|
|||
|
|
<h5>2.RADIUS概述</h5>
|
|||
|
|
|
|||
|
|
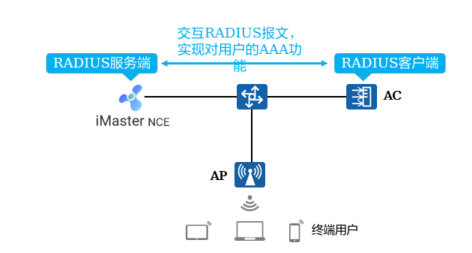
AAA可以通过多种协议来实现,在实际应用中,最常使用RADIUS协议
|
|||
|
|
|
|||
|
|
RADIUS是一种分布式的、客户端/服务器结构的信息交互协议,能保护网络不受未授权访问的干扰,常应用在既要求较高安全性、又允许远程用户访问的各种网络环境中
|
|||
|
|
|
|||
|
|
该协议定义了基于UDP(User Datagram Protocol)的RADIUS报文格式及其传输机制,并规定UDP端口1812、1813分别作为默认的认证、计费端口
|
|||
|
|
|
|||
|
|
**RADIUS协议的主要特征如下:**
|
|||
|
|
|
|||
|
|
客户端/服务器模式
|
|||
|
|
|
|||
|
|
安全的消息交互机制
|
|||
|
|
|
|||
|
|
良好的扩展性
|
|||
|
|
|
|||
|
|
|
|||
|
|
|
|||
|
|
<h5>3.802.1X认证</h5>
|
|||
|
|
|
|||
|
|
802.1X是IEEE制定的关于用户接入网络的认证标准,主要解决以太网内认证和安全方面的问题
|
|||
|
|
|
|||
|
|
802.1X认证系统为典型的Client/Server结构,包括3个实体:请求方、认证方和认证服务器
|
|||
|
|
|
|||
|
|
认证服务器通常是RADIUS服务器,用于对申请者进行认证、授权和计费
|
|||
|
|
|
|||
|
|
对于大中型企业的员工,推荐使用802.1X认证
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
<h5>4.MAC认证</h5>
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
MAC认证是一种基于MAC地址对用户的网络访问权限进行控制的认证方法,它不需要用户安装任何客户端软件
|
|||
|
|
|
|||
|
|
接入设备在启动了MAC认证的接口上首次检测到用户的MAC地址后,即启动对该用户的认证操作
|
|||
|
|
|
|||
|
|
认证过程中,不需要用户手动输入用户名或者密码
|
|||
|
|
|
|||
|
|
MAC认证常用于哑终端(如打印机)的接入认证,或者结合认证服务器完成MAC优先的Portal认证,用户首次认证通过后,一定时间内免认证再次接入
|
|||
|
|
|
|||
|
|
<h5>5.Portal认证</h5>
|
|||
|
|
|
|||
|
|
Portal认证通常也称为Web认证,将浏览器作为认证客户端,不需要安装单独的认证客户端
|
|||
|
|
|
|||
|
|
用户上网时,必须在Portal页面进行认证,只有认证通过后才可以使用网络资源,同时服务提供商可以在Portal页面上开展业务拓展,如展示商家广告等
|
|||
|
|
|
|||
|
|
对于大中型企业的访客、商业会展和公共场所,推荐使用Portal认证
|
|||
|
|
|
|||
|
|
**常用的Portal认证方式如下:**
|
|||
|
|
|
|||
|
|
用户名和密码方式:由前台管理员给访客申请一个临时账号,访客使用临时账号认证
|
|||
|
|
|
|||
|
|
短信认证:访客通过手机验证码方式认证
|
|||
|
|
|
|||
|
|

|
|||
|
|
|
|||
|
|
<h5>6.MAC优先的Portal认证</h5>
|
|||
|
|
|
|||
|
|
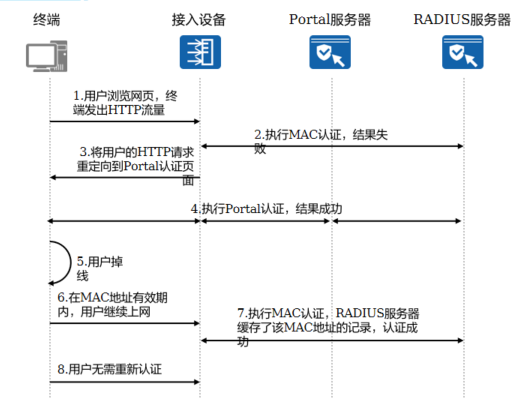
|
|||
|
|
|
|||
|
|
**技术背景**
|
|||
|
|
|
|||
|
|
用户进行Portal认证成功后,如果断开网络,重新连接时需要再次输入用户名、密码,体验差。
|
|||
|
|
|
|||
|
|
**MAC优先的Portal认证**
|
|||
|
|
|
|||
|
|
用户进行Portal认证成功后,在一定时间内断开网络重新连接,能够直接通过MAC认证接入,无需输入用户名密码重新进行Portal**认证**
|
|||
|
|
|
|||
|
|
该功能需要在设备配置MAC+Portal的混合认证,同时在认证服务器上开启MAC优先的Portal认证功能并配置MAC地址有效时间
|
|||
|
|
|
|||
|
|
<h5>7.三种认证方式比较</h5>
|
|||
|
|
|
|||
|
|
NAC包括三种认证方式:802.1X认证、MAC认证和Portal认证。由于三种认证方式认证原理不同,各自适合的场景也有所差异,实际应用中,可以根据场景部署某一种合适的认证方式,也可以部署几种认证方式组成的混合认证,混合认证的组合方式以设备实际支持为准
|
|||
|
|
|
|||
|
|
| **对比项** | **802.1X**认证 | **MAC**认证 | **Portal**认证 |
|
|||
|
|
| ---------- | ------------------------------------------ | ------------------------------------ | ---------------------------- |
|
|||
|
|
| 适合场景 | 新建网络、用户集中、信息安全要求严格的场景 | 打印机、传真机等哑终端接入认证的场景 | 用户分散、用户流动性大的场景 |
|
|||
|
|
| 客户端需求 | 需要 | 不需要 | 不需要 |
|
|||
|
|
| 优点 | 安全性高 | 无需安装客户端 | 部署灵活 |
|
|||
|
|
| 缺点 | 部署不灵活 | 需登记MAC地址,管理复杂 | 安全性不高 |
|