上传文件至 'zabbix-md'
This commit is contained in:
parent
7863550162
commit
7638f3d7a4
115
zabbix-md/zabbix-proxy部署.md
Normal file
115
zabbix-md/zabbix-proxy部署.md
Normal file
@ -0,0 +1,115 @@
|
|||||||
|
<h1><center>Zabbix-Proxy部署</center></h1>
|
||||||
|
|
||||||
|
------
|
||||||
|
|
||||||
|
**作者:行癫(盗版必究)**
|
||||||
|
|
||||||
|
## 一:环境准备
|
||||||
|
|
||||||
|
| 主机名 | 地址 |
|
||||||
|
| :-----------: | :----------: |
|
||||||
|
| zabbix-server | 10.36.174.13 |
|
||||||
|
| zabbix-proxy | 10.36.174.24 |
|
||||||
|
| zabbix-agent | 10.36.174.23 |
|
||||||
|
| zabbix-mysql | 10.36.174.90 |
|
||||||
|
|
||||||
|
<img src="https://xingdian-image.oss-cn-beijing.aliyuncs.com/xingdian-image/image-20230301172434027.png" alt="image-20230301172434027" style="zoom:80%;" />
|
||||||
|
|
||||||
|
## 二:部署Zabbix-server
|
||||||
|
|
||||||
|
略
|
||||||
|
|
||||||
|
## 三:部署Zabbix-proxy
|
||||||
|
|
||||||
|
#### 1.准备仓库
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@zabbix_proxy ~]# rpm -Uvh https://repo.zabbix.com/zabbix/5.0/rhel/7/x86_64/zabbix-release-5.0-1.el7.noarch.rpm
|
||||||
|
```
|
||||||
|
|
||||||
|
#### 2.安装zabbix-proxy
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@zabbix_proxy ~]# yum install zabbix-proxy-mysql -y
|
||||||
|
```
|
||||||
|
|
||||||
|
#### 3.安装数据库
|
||||||
|
|
||||||
|
略
|
||||||
|
|
||||||
|
#### 4.配置数据库
|
||||||
|
|
||||||
|
```shell
|
||||||
|
mysql> create database zabbix_proxy character set utf8 collate utf8_bin;
|
||||||
|
mysql> grant all on zabbix_proxy.* to zabbix_proxy@'%' identified by '123456';
|
||||||
|
```
|
||||||
|
|
||||||
|
注意:
|
||||||
|
|
||||||
|
本次使用的是单独的数据库服务器,需要在数据库服务器上授权远程登录
|
||||||
|
|
||||||
|
#### 5.配置zabbix-proxy
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@zabbix_proxy ~]# vim /etc/zabbix/zabbix_proxy.conf
|
||||||
|
ProxyMode=0 开启主动模式
|
||||||
|
Server=10.36.174.13 指定zabbix-server地址
|
||||||
|
Hostname=zabbix_proxy 设定名字
|
||||||
|
DBHost=10.36.174.90 指定数据库地址
|
||||||
|
DBName=zabbix_proxy 指定数据库库名
|
||||||
|
DBUser=zabbix_proxy 指定数据库用户
|
||||||
|
DBPassword=123456 指定数据库密码
|
||||||
|
```
|
||||||
|
|
||||||
|
#### 6.重启服务
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@zabbix_proxy ~]# systemctl restart zabbix-proxy
|
||||||
|
```
|
||||||
|
|
||||||
|
## 四:部署zabbix-agent
|
||||||
|
|
||||||
|
#### 1.安装部署
|
||||||
|
|
||||||
|
略
|
||||||
|
|
||||||
|
#### 2.修改配置文件
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@zabbix_agent ~]# vim /etc/zabbix/zabbix_agentd.conf 指向proxy地址
|
||||||
|
Server=10.36.174.24
|
||||||
|
ServerActive=10.36.174.24
|
||||||
|
Hostname=Zabbix-agent-2
|
||||||
|
```
|
||||||
|
|
||||||
|
#### 3.重启服务
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@zabbix_agent~]# systemctl restart zabbix-agent
|
||||||
|
```
|
||||||
|
|
||||||
|
## 五:部署zabbix-server
|
||||||
|
|
||||||
|
#### 1.添加agent代理程序
|
||||||
|
|
||||||
|
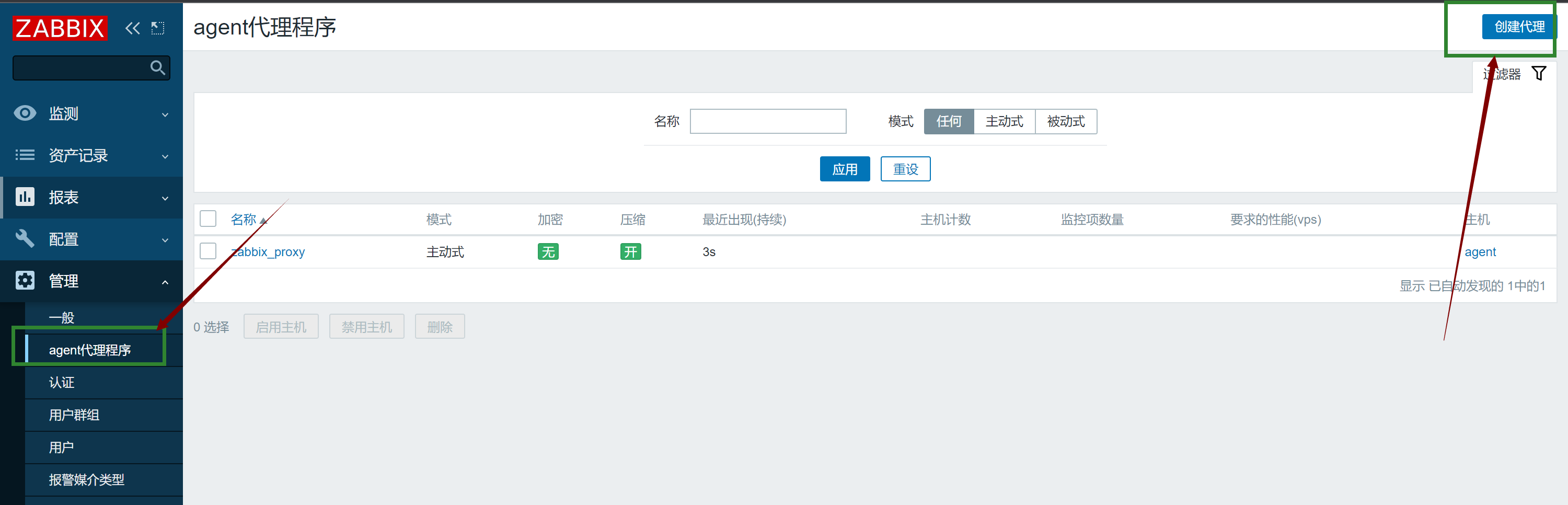
|
||||||
|
|
||||||
|
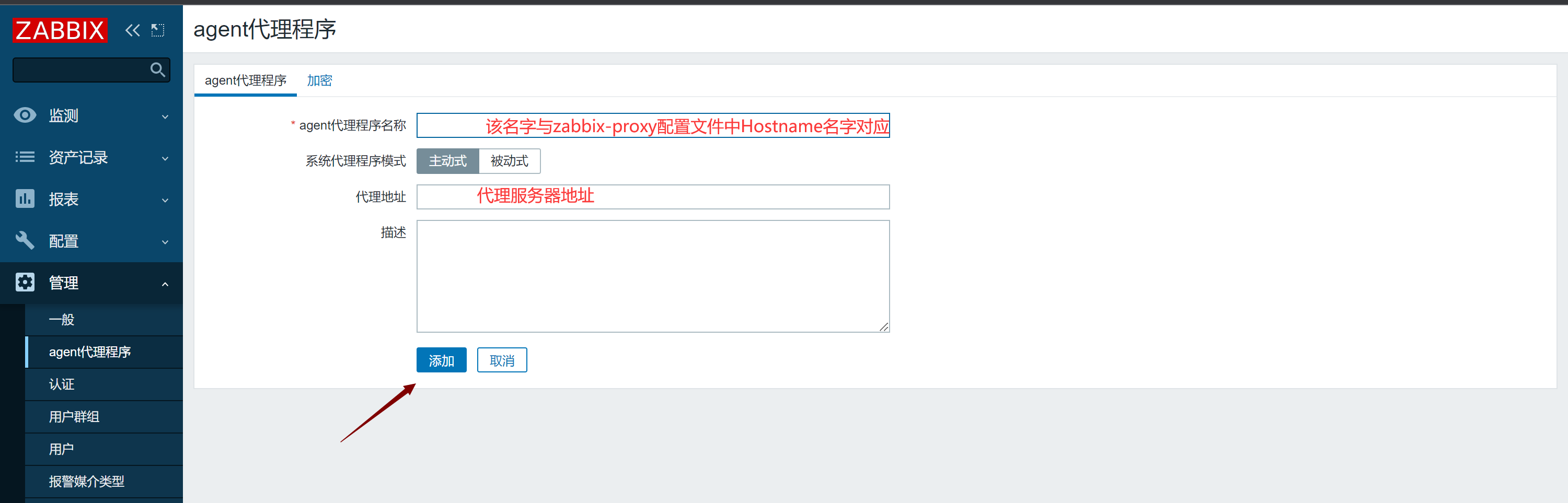
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
#### 2.配置监控主机使用代理
|
||||||
|
|
||||||
|
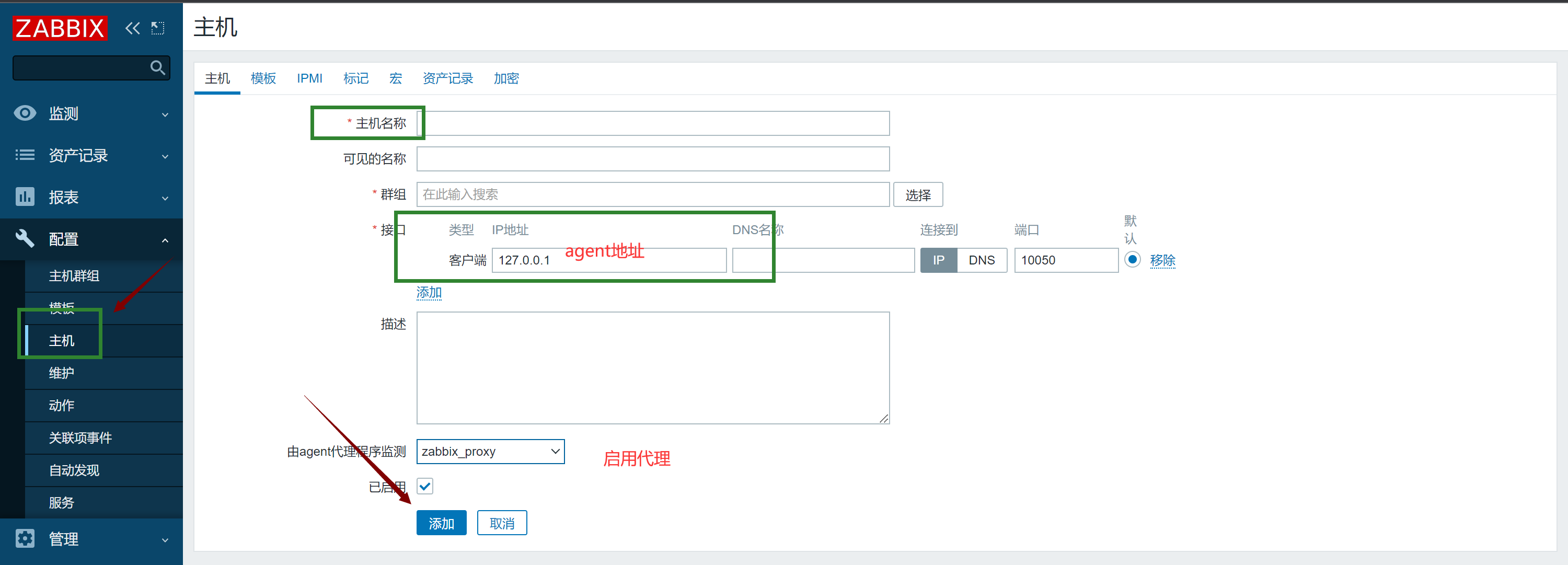
|
||||||
|
|
||||||
|
#### 3.配置监控项
|
||||||
|
|
||||||
|
略(检测是否可以使用代理获取数据)
|
||||||
|
|
||||||
|
#### 4.配置图形展示
|
||||||
|
|
||||||
|
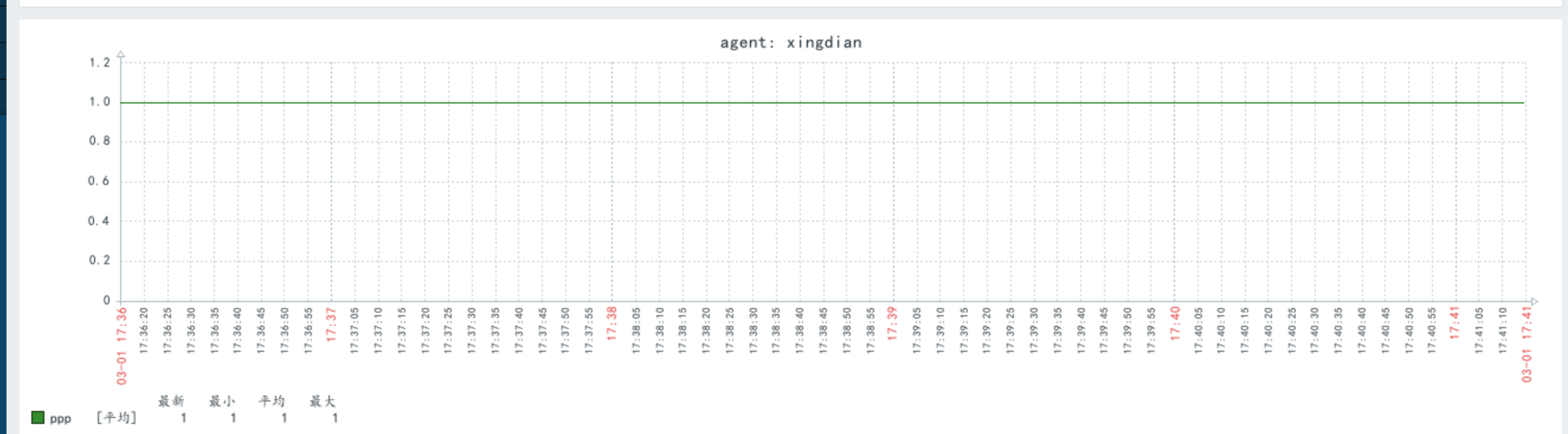
略(检测是否可以使用代理获取数据)
|
||||||
|
|
||||||
|
<img src="https://xingdian-image.oss-cn-beijing.aliyuncs.com/xingdian-image/image-20230301174101767.png" alt="image-20230301174101767" style="zoom:100%;" />
|
||||||
|
|
||||||
|
|
||||||
144
zabbix-md/zabbix邮箱报警.md
Normal file
144
zabbix-md/zabbix邮箱报警.md
Normal file
@ -0,0 +1,144 @@
|
|||||||
|
<h1><center>Zabbix邮箱报警</center></h1>
|
||||||
|
|
||||||
|
------
|
||||||
|
|
||||||
|
**作者:行癫(盗版必究)**
|
||||||
|
|
||||||
|
## 一:环境准备
|
||||||
|
|
||||||
|
#### 1.监控环境
|
||||||
|
|
||||||
|
zabbix-server正常运行,并且正常对zabbix-agent进行监控
|
||||||
|
|
||||||
|
#### 2.注册163邮箱
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
注册邮箱设置客户端授权密码
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 二:邮箱部署
|
||||||
|
|
||||||
|
#### 1.软件安装
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@xingdian ~]# yum install mailx -y
|
||||||
|
```
|
||||||
|
|
||||||
|
#### 2.邮箱配置
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@xingdian ~]# vim /etc/mail.rc
|
||||||
|
set from=lisi@163.com(邮箱地址)
|
||||||
|
set smtp=smtp.163.com(smtp服务器)
|
||||||
|
set smtp-auth-user=lisi@163.com(用户名)
|
||||||
|
set smtp-auth-password=*(授权邮箱密码)
|
||||||
|
set smtp-auth=login
|
||||||
|
```
|
||||||
|
|
||||||
|
#### 3.发邮件的方式
|
||||||
|
|
||||||
|
```shell
|
||||||
|
方式1:mailx -s "邮件标题" 收件箱Email < 包含正文的文件
|
||||||
|
方式2:cat 包含正文的文件 | mailx -s "邮件标题" 收件箱Email
|
||||||
|
方式3:echo "正文内容" | mailx -s "邮件标题" 收件箱Email
|
||||||
|
方式4:mailx -s "邮件标题" 收件箱Email,回车按CTRL+D发送
|
||||||
|
```
|
||||||
|
|
||||||
|
#### 4.手动测试
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@xingdian ~]# mailx -v -s 'hello' 'zhangsan@163.com'
|
||||||
|
nihao (回车,然后ctrl+D
|
||||||
|
EOT
|
||||||
|
或者,将邮件内容放到一个文件中content.txt
|
||||||
|
# cat content.txt | mailx -v -s ‘hello’ ‘zhangsan@163.com’
|
||||||
|
```
|
||||||
|
|
||||||
|
#### 5.创建告警脚本
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@xingdian ~]# cd /usr/lib/zabbix/alertscripts
|
||||||
|
[root@xingdian ~]# vim sendmail.sh
|
||||||
|
#!/bin/sh
|
||||||
|
echo "$3" | sed s/'\r'//g | mailx -s "$2" $1
|
||||||
|
[root@xingdian ~]# chmod u+x sendmail.sh && chown zabbix.zabbix sendmail.sh
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 三:部署Zabbix监控
|
||||||
|
|
||||||
|
#### 1.创建主机群组
|
||||||
|
|
||||||
|
#### 2.创建主机
|
||||||
|
|
||||||
|
#### 3.创建监控项
|
||||||
|
|
||||||
|
(监控nginx服务是否正常运行)
|
||||||
|
|
||||||
|
#### 4.创建触发器
|
||||||
|
|
||||||
|
#### 5.创建报警媒介
|
||||||
|
|
||||||
|
脚本参数:
|
||||||
|
|
||||||
|
{ALERT.SENDTO}
|
||||||
|
|
||||||
|
{ALERT.SUBJECT}
|
||||||
|
|
||||||
|
{ALERT.MESSAGE}
|
||||||
|
|
||||||
|
#### 6.创建动作
|
||||||
|
|
||||||
|
关联触发器
|
||||||
|
|
||||||
|
添加操作
|
||||||
|
|
||||||
|
```shell
|
||||||
|
"主题"对应"钉钉告警"媒介中的:{ALERT.SUBJECT}
|
||||||
|
"消息"对应"钉钉告警"媒介中的:{ALERT.MESSAGE}
|
||||||
|
|
||||||
|
主题:
|
||||||
|
|
||||||
|
故障名称(触发器名称):{EVENT.NAME}
|
||||||
|
|
||||||
|
消息:
|
||||||
|
|
||||||
|
告警主机:{HOSTNAME1}
|
||||||
|
告警时间:{EVENT.DATE} {EVENT.TIME}
|
||||||
|
告警等级:{TRIGGER.SEVERITY}
|
||||||
|
告警信息: {TRIGGER.NAME}
|
||||||
|
告警项目:{TRIGGER.KEY1}
|
||||||
|
问题详情:{ITEM.NAME}:{ITEM.VALUE}
|
||||||
|
当前状态:{TRIGGER.STATUS}:{ITEM.VALUE1}
|
||||||
|
事件ID:{EVENT.ID}
|
||||||
|
```
|
||||||
|
|
||||||
|
添加恢复操作
|
||||||
|
|
||||||
|
```shell
|
||||||
|
主题:故障恢复:{EVENT.NAME}
|
||||||
|
|
||||||
|
消息:
|
||||||
|
|
||||||
|
恢复主机:{HOSTNAME1}
|
||||||
|
恢复时间:{EVENT.DATE} {EVENT.TIME}
|
||||||
|
主机IP:{HOST.IP}
|
||||||
|
告警项目:{TRIGGER.KEY1}
|
||||||
|
问题详情:{ITEM.NAME}:{ITEM.VALUE}
|
||||||
|
当前状态:{TRIGGER.STATUS}:{ITEM.VALUE1}
|
||||||
|
事件ID:{EVENT.ID}
|
||||||
|
```
|
||||||
|
|
||||||
|
#### 7.用户关联报警媒介
|
||||||
|
|
||||||
|
#### 8.模拟报警产生
|
||||||
|
|
||||||
|
#### 9.查看报警信息
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
247
zabbix-md/zabbix钉钉报警.md
Normal file
247
zabbix-md/zabbix钉钉报警.md
Normal file
@ -0,0 +1,247 @@
|
|||||||
|
<h1><center>Zabbix钉钉报警</center></h1>
|
||||||
|
|
||||||
|
------
|
||||||
|
|
||||||
|
**作者:行癫(盗版必究)**
|
||||||
|
|
||||||
|
## 一:环境准备
|
||||||
|
|
||||||
|
#### 1.监控环境
|
||||||
|
|
||||||
|
zabbix-server正常运行,并且正常对zabbix-agent进行监控
|
||||||
|
|
||||||
|
#### 2.注册钉钉
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
安装钉钉PC端,注册账户,添加好友(至少3好友)
|
||||||
|
|
||||||
|
创建群组
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
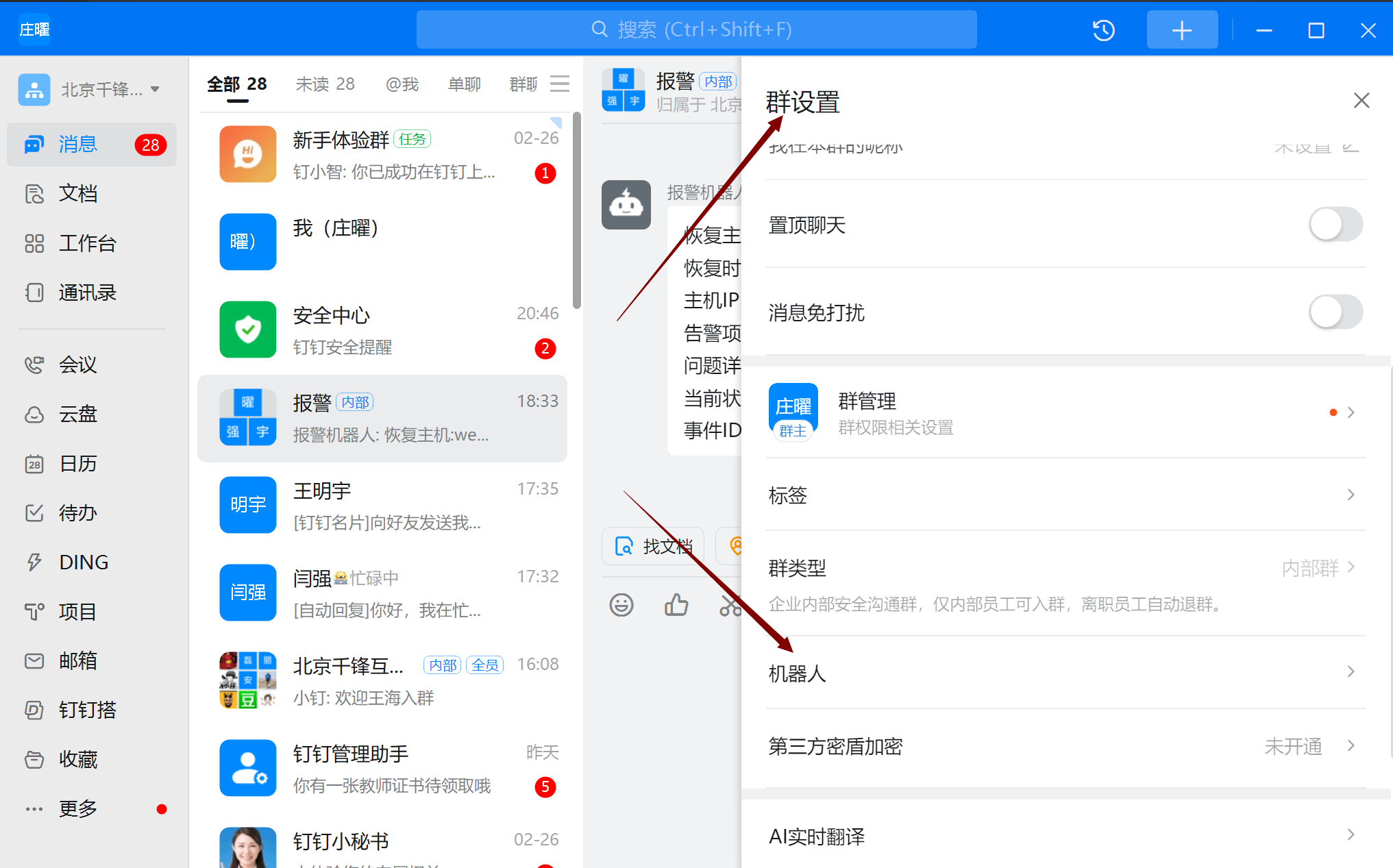
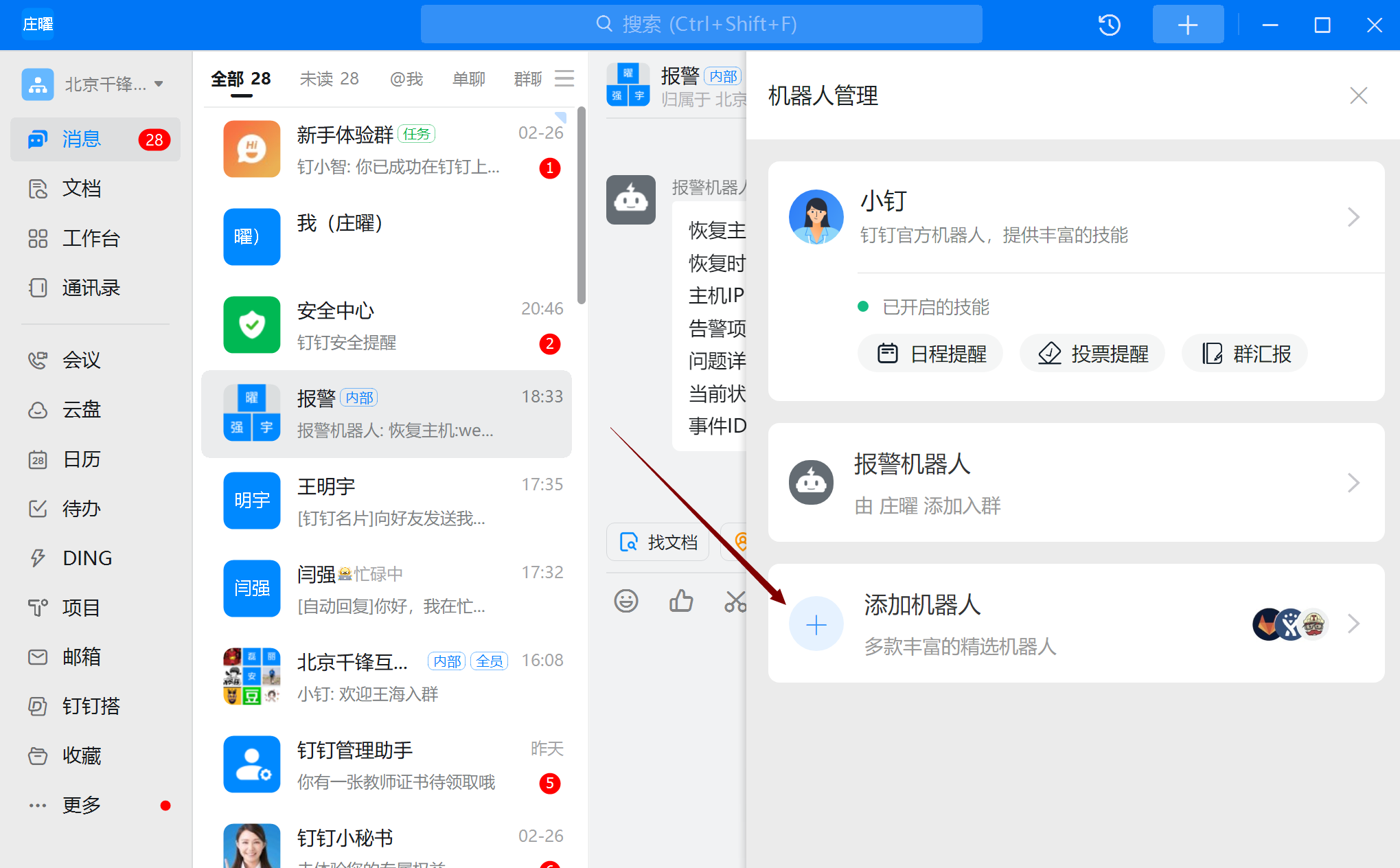
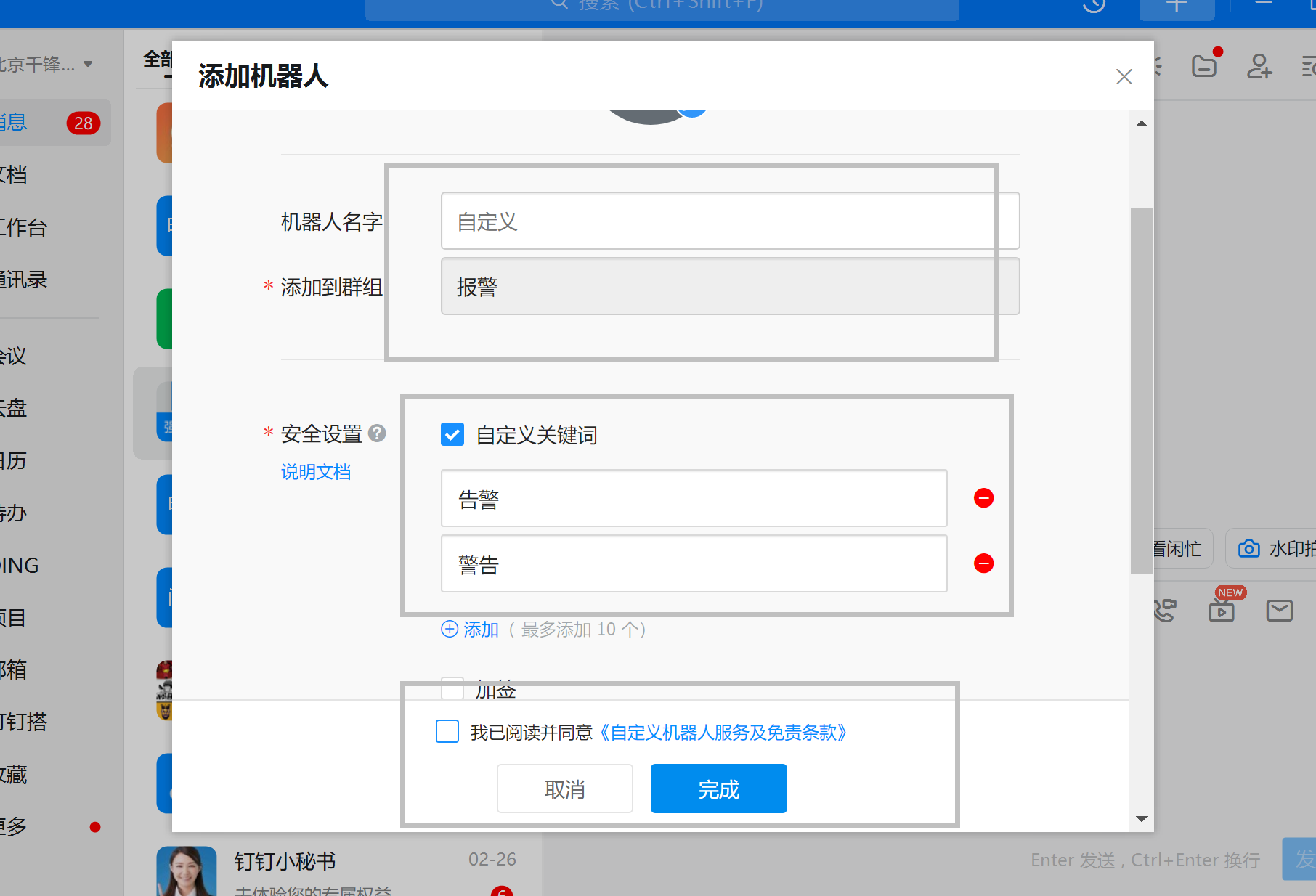
创建机器人
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
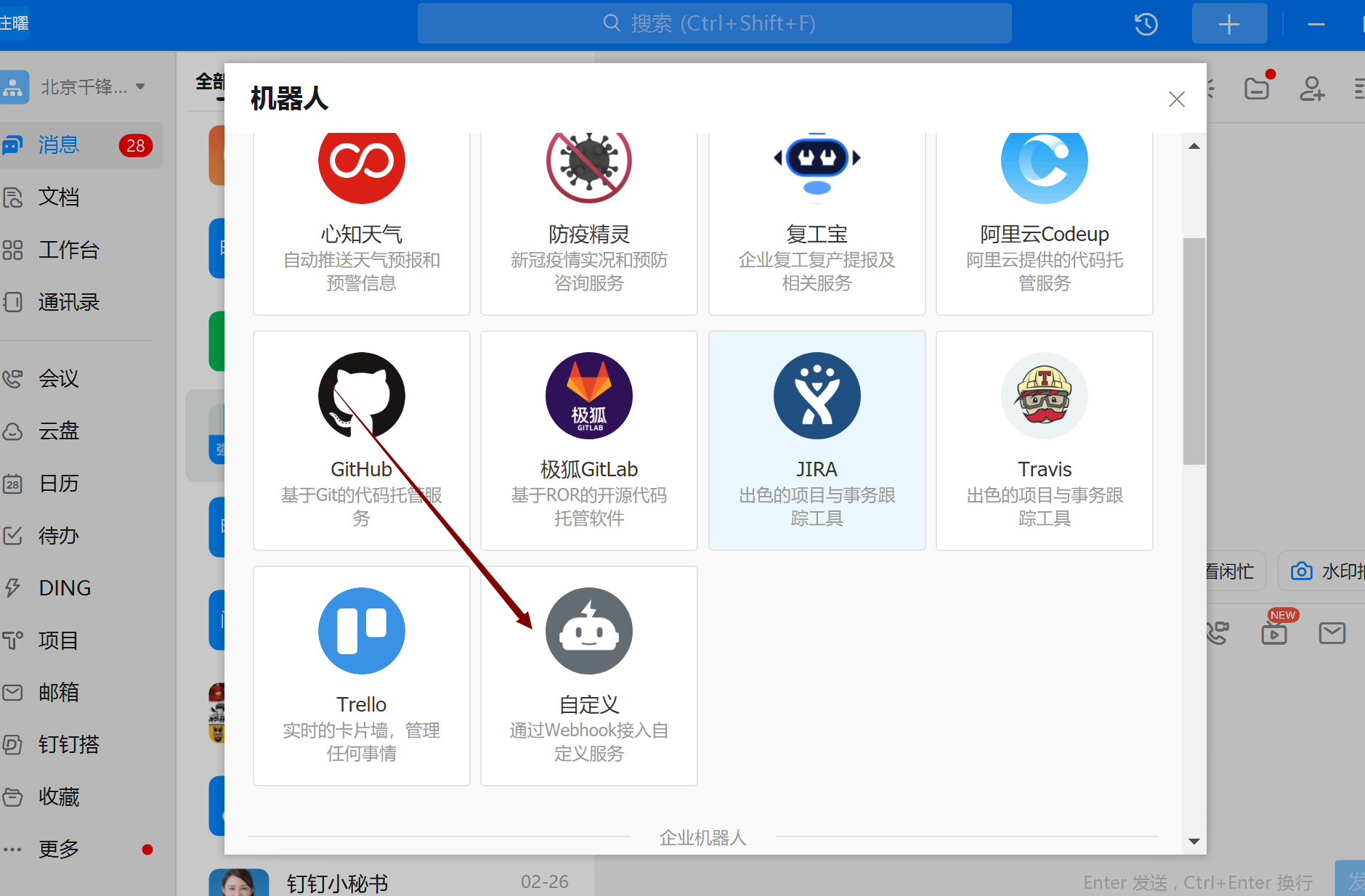
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
注意:保存webhook
|
||||||
|
|
||||||
|
#### 3.python3环境
|
||||||
|
|
||||||
|
安装python3
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@xingdian ~]# yum -y install python3
|
||||||
|
[root@xingdian ~]# yum -y install python-pip
|
||||||
|
```
|
||||||
|
|
||||||
|
更换pip源
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@xingdian ~]# mkdir ~/.pip
|
||||||
|
[root@xingdian ~]# vim ~/.pip/pip.conf
|
||||||
|
[global]
|
||||||
|
index-url=http://mirrors.aliyun.com/pypi/simple/
|
||||||
|
|
||||||
|
[install]
|
||||||
|
trusted-host=mirrors.aliyun.com
|
||||||
|
```
|
||||||
|
|
||||||
|
安装requests模块
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@xingdian ~]# pip install --upgrade pip
|
||||||
|
[root@xingdian ~]# pip install requests
|
||||||
|
```
|
||||||
|
|
||||||
|
#### 4.配置监控脚本
|
||||||
|
|
||||||
|
创建钉钉脚本
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@xingdian ~]# cd /usr/lib/zabbix/alertscripts/
|
||||||
|
[root@xingdian alertscripts]# vim dingding.py
|
||||||
|
|
||||||
|
#!/usr/bin/python
|
||||||
|
|
||||||
|
#-*- coding: utf-8 -*-
|
||||||
|
|
||||||
|
#zabbix钉钉报警
|
||||||
|
import requests,json,sys,os,datetime
|
||||||
|
|
||||||
|
webhook="https://oapi.dingtalk.com/robot/send?access_token=feb43aea482d9da72e781d92dbfc074f701642a166f31194ff347954f500a404"
|
||||||
|
|
||||||
|
#说明:这里改为自己创建的机器人的webhook的值
|
||||||
|
|
||||||
|
user=sys.argv[1]
|
||||||
|
|
||||||
|
#发给钉钉群中哪个用户
|
||||||
|
|
||||||
|
text=sys.argv[3]
|
||||||
|
|
||||||
|
#发送的报警内容
|
||||||
|
|
||||||
|
data={
|
||||||
|
|
||||||
|
"msgtype": "text",
|
||||||
|
|
||||||
|
"text": {
|
||||||
|
|
||||||
|
"content": text
|
||||||
|
|
||||||
|
},
|
||||||
|
|
||||||
|
"at": {
|
||||||
|
|
||||||
|
"atMobiles": [
|
||||||
|
|
||||||
|
user
|
||||||
|
|
||||||
|
],
|
||||||
|
|
||||||
|
"isAtAll": False
|
||||||
|
|
||||||
|
}
|
||||||
|
|
||||||
|
}
|
||||||
|
|
||||||
|
#钉钉API固定数据格式
|
||||||
|
|
||||||
|
headers = {'Content-Type': 'application/json'}
|
||||||
|
|
||||||
|
x=requests.post(url=webhook,data=json.dumps(data),headers=headers)
|
||||||
|
|
||||||
|
if os.path.exists("/var/log/zabbix/dingding.log"):
|
||||||
|
|
||||||
|
f=open("/var/log/zabbix/dingding.log","a+")
|
||||||
|
|
||||||
|
else:
|
||||||
|
|
||||||
|
f=open("/var/log/zabbix/dingding.log","w+")
|
||||||
|
|
||||||
|
f.write("\n"+"--"*30)
|
||||||
|
|
||||||
|
if x.json()["errcode"] == 0:
|
||||||
|
|
||||||
|
f.write("\n"+str(datetime.datetime.now())+" "+str(user)+" "+"发送成功"+"\n"+str(text))
|
||||||
|
|
||||||
|
f.close()
|
||||||
|
|
||||||
|
else:
|
||||||
|
|
||||||
|
f.write("\n"+str(datetime.datetime.now()) + " " + str(user) + " " + "发送失败" + "\n" + str(text))
|
||||||
|
|
||||||
|
f.close()
|
||||||
|
|
||||||
|
#将发送的告警信息写入本地日志/var/log/zabbix/dingding.log中
|
||||||
|
|
||||||
|
[root@xingdian alertscripts]# chmod +x dingding.py
|
||||||
|
```
|
||||||
|
|
||||||
|
创建日志文件
|
||||||
|
|
||||||
|
```shell
|
||||||
|
[root@xingdian alertscripts]# touch /var/log/zabbix/dingding.log
|
||||||
|
[root@xingdian alertscripts]# chown zabbix.zabbix /var/log/zabbix/dingding.log
|
||||||
|
```
|
||||||
|
|
||||||
|
测试命令
|
||||||
|
|
||||||
|
```shell
|
||||||
|
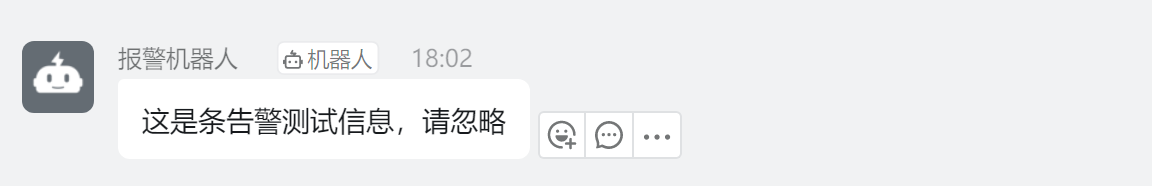
[root@xingdian alertscripts]# ./dingding.py xingdian test "这是条告警测试信息,请忽略"
|
||||||
|
```
|
||||||
|
|
||||||
|
参数说明
|
||||||
|
|
||||||
|
xingdian:钉钉群中任意一个人员的钉钉号
|
||||||
|
|
||||||
|
test:这里因脚本中没有设置接收参数,所以无实际意义,仅仅起到变量占位的作用
|
||||||
|
|
||||||
|
"这是条告警测试信息,请忽略":这是具体的告警信息,告警信息必须包含“安全设置”中自己设置的“自定义关键词”
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 二:配置Zabbix监控
|
||||||
|
|
||||||
|
#### 1.创建主机群组
|
||||||
|
|
||||||
|
#### 2.创建主机
|
||||||
|
|
||||||
|
#### 3.创建监控项
|
||||||
|
|
||||||
|
(监控nginx服务是否正常运行)
|
||||||
|
|
||||||
|
#### 4.创建触发器
|
||||||
|
|
||||||
|
#### 5.创建报警媒介
|
||||||
|
|
||||||
|
脚本参数:
|
||||||
|
|
||||||
|
```shell
|
||||||
|
{ALERT.SENDTO}
|
||||||
|
#对应脚本中的,user=sys.argv[1](发给钉钉群中哪个用户)
|
||||||
|
{ALERT.SUBJECT}
|
||||||
|
#代表发送的信息的标题,在"报表"的"动作日志"中可以看到
|
||||||
|
{ALERT.MESSAGE}
|
||||||
|
#对应脚本中的,text=sys.argv[3](发送的报警内容)
|
||||||
|
```
|
||||||
|
|
||||||
|
#### 6.创建动作
|
||||||
|
|
||||||
|
关联触发器
|
||||||
|
|
||||||
|
添加操作
|
||||||
|
|
||||||
|
```shell
|
||||||
|
"主题"对应"钉钉告警"媒介中的:{ALERT.SUBJECT}
|
||||||
|
"消息"对应"钉钉告警"媒介中的:{ALERT.MESSAGE}
|
||||||
|
|
||||||
|
主题:
|
||||||
|
|
||||||
|
故障名称(触发器名称):{EVENT.NAME}
|
||||||
|
|
||||||
|
消息:
|
||||||
|
|
||||||
|
告警主机:{HOSTNAME1}
|
||||||
|
告警时间:{EVENT.DATE} {EVENT.TIME}
|
||||||
|
告警等级:{TRIGGER.SEVERITY}
|
||||||
|
告警信息: {TRIGGER.NAME}
|
||||||
|
告警项目:{TRIGGER.KEY1}
|
||||||
|
问题详情:{ITEM.NAME}:{ITEM.VALUE}
|
||||||
|
当前状态:{TRIGGER.STATUS}:{ITEM.VALUE1}
|
||||||
|
事件ID:{EVENT.ID}
|
||||||
|
```
|
||||||
|
|
||||||
|
添加恢复操作
|
||||||
|
|
||||||
|
```shell
|
||||||
|
主题:故障恢复:{EVENT.NAME}
|
||||||
|
|
||||||
|
消息:
|
||||||
|
|
||||||
|
恢复主机:{HOSTNAME1}
|
||||||
|
恢复时间:{EVENT.DATE} {EVENT.TIME}
|
||||||
|
主机IP:{HOST.IP}
|
||||||
|
告警项目:{TRIGGER.KEY1}
|
||||||
|
问题详情:{ITEM.NAME}:{ITEM.VALUE}
|
||||||
|
当前状态:{TRIGGER.STATUS}:{ITEM.VALUE1}
|
||||||
|
事件ID:{EVENT.ID}
|
||||||
|
```
|
||||||
|
|
||||||
|
#### 7.用户关联报警媒介
|
||||||
|
|
||||||
|
#### 8.模拟报警产生
|
||||||
|
|
||||||
|
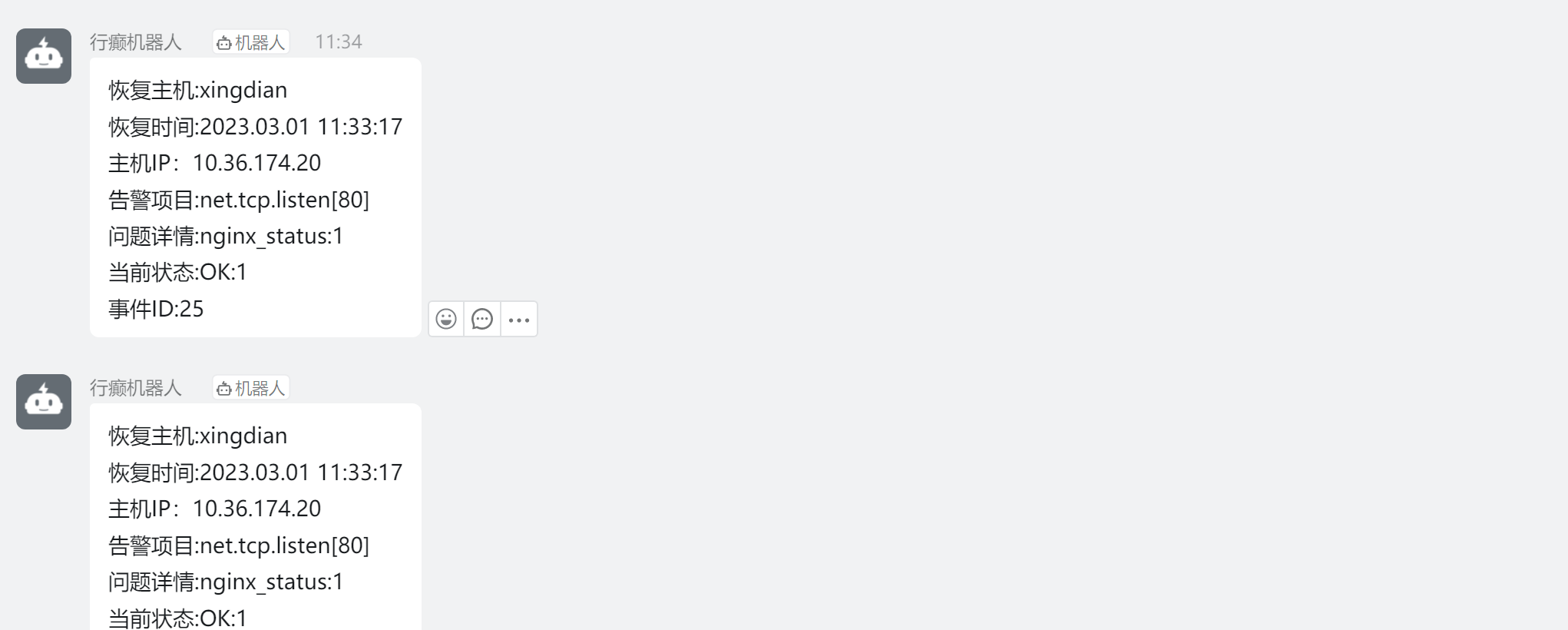
#### 9.查看报警信息
|
||||||
|
|
||||||
|
|
||||||
Loading…
Reference in New Issue
Block a user